Central Banking and the Digital Currency Choices
Central Banking and the Digital Currency Choices. The Pros. & Cons.
Adan Salman
2022
Article Review
Design Choices for Central Bank Digital Currency Policy and Technical Considerations
July 23, 2020, v1.0
Sarah Allen1, Srdjan Capkun 2,1, Ittay Eyal 3,1, Giulia Fanti 4,1, Bryan Ford 5,1, James Grimmelmann 6,1, Ari Juels 10,1, Kari Kostiainen 2,1, Sarah Meiklejohn 7,1, Andrew Miller 8,1, Eswar Prasad9, Karl Wüst 2,1, and Fan Zhang 10,1
1Initiative for Crypto Currencies and Contracts (IC3); 2Swiss Federal Institute of Technology in Zürich (ETH Zürich); 3Israel Institute of Technology (Technion); 4Carnegie Mellon University (CMU); 5Swiss Federal Institute of Technology in Lausanne (EPFL); 6Cornell Tech and Cornell Law School; 7University College London (UCL); 8University of Illinois at Urbana-Champaign (UIUC); 9Cornell University and Brookings Institution; 10Cornell Tech.
Abstract
In this review we have covered an extensive research and planning of a potential utilization of Central Bank Digital Currency (CBDC) with detailed promotion for their use and advantages for financial security and stability.
Digital processing of transactions, which has been in use for some time on credit and money transfer systems can fully function with no need for a physical currency like bank notes or metals. Still bottom line connection to reality is very important. Going 100% virtual may vaporize reality for the humans themselves.
Meanwhile, the paper – Design choices for Central Bank Digital Currency, Policy and technical considerations, has shown objective and technical analysis and raised risks and issues (1). Their bottom line is summarized in a very expressive statement
“The issuance of CBDC will not in any way mask underlying weaknesses in central bank credibility or other issues such as fiscal dominance that affect the value of cash. In other words, digital central bank money is only as strong and credible as the central bank that issues it”.
“In summary, the benefits and risks of CBDC are complex, encompassing an interplay among financial, legal, and technical considerations. Each country will have to take into account its specific circumstances and initial conditions before deciding whether the potential benefits of introducing a CBDC outweigh the possible costs.”
The paper provides a reasonable review of positions that are inclined to the concept for adopting CBDC, but with credible issues to consider before going full digital. Another article that showed a strong conceptual support position with little technical justification (2) did not clear the risks associated. We did not include its review due to space limitations. We have raised other conceptual points to balance the review and give a truly neutral evaluation. We consulted with other works (3-5) related to the benefits and risks of the transformation toward digital currencies including central control and the hard availability of credit, or liquidity of cash outside the banks control.
These can create super controlling situations that can suffocate the middle class capacity for production. It seems the CBDC work is well suited to serve mega rich financial institutions, because it will simplify the movement of the funds with simple tracking protocols. As it seems, still small errors can erase a lot of the safety measures.
Global universal central currency seems to offer a solution, but the problems connected to implementation require full control and power, and hence these forms of financial transactions are not compatible with the flexibility and freedom of standards we know and are accustomed to.
Accordingly, we give a somber approach towards evaluation. Digital banking is a good service, but digital currencies with no material alternatives for daily use of humans transactions is not. We recommend strongly going back to gold standard and strong correlation between paper currency printout, and true economic worth of economies, while utilizing the digital advantage to a full extent in service of the humanity, and not the controllers or the machines.
Contents
Central Banking and the Digital Currency Choices. The Pros. & Cons. 1
II. Review Summaries and Our Comments 4
II.2 Our Evaluation and Comments on the Article 7
III. Evaluation and CBDC Comparison with Other Currency Representations 9
III.1 Design of CBDC and Impact on Economic and Social Indicators 9
III.2 Potential Successes and Failures 10
III.3 Comparison With Paper Currency or Connection to Metals and Gold 10
III.4 Conclusions and Recommendations 11
4. Account and Identity Management 16
6. Privacy and Transparency 20
9. Novel Financial Technology 27
I. Introduction
The introduction of central bank digital currency operation as defined, is assigning nominal currency values that do not require paper notes printing or other standards of economic indicators. These would be values assigned to the available wealth in the country. The amount and limit to this value is flexible and does not show true indicators beyond transfers of numbers from one account to another. The controlling body in charge is mainly the only authority that can increase or decrease the valuable amounts or the total. The customers using the funds get numbers that cannot be cashed but can purchase materials through direct transaction systems that accept such operations.
For a single nation central bank, there would be a strong need by many to connect to more powerful economies to protect their financial values from drying. Loans can eat their final assets as automatic transfers. Small entities cannot survive the ecosystem and hence a central universal system is highly assumed as the end result. This means the whole world would be under a single banking entity.
The comparison with notes shows some differences. If the country prints some notes, they have to honor them if deposited or cashed back from their banks. In that sense people or companies can keep some of the cash outside the central bank access or control.
Small economies can lose their currencies if some brokers collect large fractions of all cash in the market and just remove it from exchange. It is hard but possible. Accordingly, such shortage can increase the currency value and the speculator can gain good profits and recollect using a stable currency or asset.
In CBDC, this can happen by speculators too. But the central bank can allocate such funds because it can trace all transactions and catch and apply certain rules to get the amounts back, and that is good. But here is the catch. If the central bank wants to play this game it will be possible 100% to do whatever they like. This means CBDCs can get orders of magnitude of control by the central bank over any other alternative system This is one of the main challenges. It gets worse if the whole world is governed by a single bank and currency even if not directly.
Now if we compare this type of monetary system with a system that is organically connected to a true economy mainly measured by the productive sector output and valuable metals and resources, or even paper currencies, the degree of control will be much less. Paper currencies still can flunk if the country prints too much money with no coverage, which ends up with inflation, but it can always hold the money it controls to prevent such high flow.
The work is divided into 4 sections including this introduction. Section II summarizes the essence of the review including our comments and opinions related to certain issues raised in the reviews. One should be able to get a reasonable summary of the articles and our positions.
Section III provides some comparisons with other forms of currencies regarding basic healthy financial systems performance. In this section we compare designs that take into account the articles suggestions. Comparisons include papers notes, metals, natural resources, and the productive sector representation of wealth. Section IV provides the detailed reviews of the article. It is detailed and long and the review preserved the core information with the review 20% of the original.
In the detailed review, I have highlighted my comments and observations in blue within the text. These comments were collectively combined to give an overall review. Such comments are reflected in the short review in section II and the abstract. The authors have their own summaries, and they are included in their original places, in addition to inclusion in section II. I have kept the order of the sections as the original to simplify the review tracking.
II. Review Summaries and Our Comments
Design Choices for CBDC Policy and Technical Considerations
Central banks around the world are exploring or piloting CBDCs. “The promise is to realize a broad range of capabilities, including direct government disbursements to citizens, frictionless consumer payment and money-transfer systems, and a financial instruments and monetary policy levers”.
They claim also that CBDCs can give rise, however, to a host of challenging technical goals and design questions that are qualitatively and quantitatively different from those in existing government and consumer payment systems.
A working CBDC requires a resilient, secure, and functional infrastructure, with the ability to onboard, authenticate, and support users on a massive scale. It require a simple architecture to support modular design and rigorous security analysis, that is flexible to accommodate current and future functional requirements and use cases. A CBDC needs to address the innate tension between privacy and transparency, protecting user data from abuse while selectively permitting data mining for end-user services, policymakers, and law enforcement investigations and interventions. The paper counts technical design benefits and challenges for CBDC designers, in terms of performance, privacy, and security, through a survey of academic and industry R&D systems. They present the technologies that can address the problems, which may face a CBDC deployment. They envision some functionalities and use cases the CBDC can finally offer.
II.1 Article Summary
The authors explorations in the paper suggest a number of topics and issues that deserve special consideration by CBDC designers.
Used technical definition. Kumhof and Noone (2.1) define “CBDC as electronic central bank money that: (i) can be accessed more broadly than reserves, (ii) has functionality for retail transactions, (iii) can be interest bearing (with a rate different from that on reserves), and (iv) has a separate operational structure relative to other forms of money”.
Focus is on retail CBDCs. “The paper discusses and evaluates the design choices, mainly technical, but also financial and legal, that central banks will encounter in their exploration of CBDCs. Contributing authors include experts in computer science, economics, and law with practical experience in the design of digital currencies. The paper emphasizes choices, and challenges that will define CBDC deployment or realization. Both cryptocurrencies and CBDC offer evidence of feasibility for retail deployment of digital currency. The technical basis of Libra have influenced CBDC design plans, and the article recommendations”.
Envisioned benefits of using CBDC. The authors summarize them, but not all people may consider them so
- Efficiency: can reduce friction payment systems, by reducing monetary cost and increasing the speed of transactions finalization.
- Broader tax base adds more economic activity into the tax net, boost revenues, and limit tax evasion.
- Flexible monetary policy: the zero lower-bound constraint on monetary policy set by the banks can be relaxed,
- Payment backstop: to private sector managed payment systems, avoiding their breakdown during a crisis of confidence or rise in risk.
- Financial inclusion: can provide options for unbanked people to have access to electronic payment systems, and products & services.
- Novel financial technologies, particularly for regulators.
Risks. The authors suggest testing the presumed benefits against potential financial and technical issues.
- Disintermediation of the banking system: the removal of an intermediary in the supply chain by reducing transaction frictions and possibly even providing interest- bearing accounts [8]. Still many CBDC designs seem inclined toward a two-layer architecture with the CBDC as the core player, while non-governmental financial institutions manage a second layer that deals with users. Nonetheless,.
- Miscalibration of government involvement: Two-layer architecture offer financial institutions chance to innovate on top of a CBDC [10]. A CBDC connected to a central bank activities that can efficiently be managed by the private sector could limit innovation. But bankers systemic risks and incompatibilities can rise without central bank involvement.
- Risks due to lack of regulatory expertise and capacity: With increased speed and efficiency come new risks, financial and technical. Regulators may develop tools and expertise to address these risks in the face of the basic operation of the system.
- Loss of privacy: given the complexity and limitations of current privacy protection technologies, it seems likely a retail CBDC will expose sensitive information to operators. CBDC designers should consider legal and technical mitigations.
- Technological vulnerabilities or design mistakes: CBDCs will represent a technical experiment, whose risks of information security failures, and fundamental design mistakes should not be underestimated.
- Other serious risks on the policy and evolution levels needs are discussed in our evaluation section (2.1.2).
Monetary policy considerations
“The CBDC will not remove underlying shortcomings in central bank credibility or fiscal dominance that affect the cash value. Digital money is only as strong and credible as the central bank that issues it. Shifting to full digital central bank money for retail, the transition risks could be higher without stable macroeconomic and structural policies, including regulatory frameworks that are agile enough to recognize and deal with financial risks resulting from emerging new financial intermediaries. Recognizing the potential benefits, there are many unanswered issues regarding new financial technologies that may affect their structure and markets. Questions also rise regarding if retail CBDC will significantly affect monetary policy implementation and transmission. These uncertainties entail a cautious approach in adopting the CBDC concept”.
Ledger infrastructure
“Expectation is that central banks may want to keep tight control over currency issuance and transaction processing, with the ability to change or reverse transactions. Such control is highly needed given the historic risks of errors in ledger based systems, and legal requirements for handling error and fraud. In principle, tight ledger control is possible for all envisioned designs, as central bank privileges can be hard-wired. In real life permissioned ledger systems, limited to pre-designated entities, or centralized systems are the suitable choices. As multi entity permissioned systems have been not realized extensively, the authors expect central banks will opt for centralized CBDCs. The digital yuan appears to be embracing such centrality”.
“Central banks may consider use of authenticated data structures (ADSs) as an extension for centralized CBDC deployments. The central bank can distribute the ADS digest 𝑅 publicly without revealing ledger contents. It can prove the inclusion of particular transactions in the ledger with reference to 𝑅 alone, and also use 𝑅 to demonstrate it is different from forking, showing different ledger contents / balances to different entities. Forking may rise as a result of operator malfeasance or a breach, hence the proving forking is prevented can strengthen users’ confidence”.
Wallets funds and keys custody
“A democratization of cryptocurrency was built on the use of wallets and key management. To authenticate users’ transactions, it requires digital signatures which are strong tools for all computing infrastructure, and they require the secret keys. Protecting and backing up keys is a problem for many cryptography users, who tend to rely on service providers by holding users’ assets intermediaries. While CBDCs may rely on similar settings it is not clear how they can advance the goal of financial inclusion if consumers have to deal with middle institutions. Efficient methods to custody of funds and secret keys will make a definer of the CBDC future”. It appears that some designs, such as the digital yuan, may offer limited support for user- administered accounts. CBDCs would, however, make it easy to prepopulate individual accounts with funds, which would be an important first step in enrolling consumers in the financial system.
Privacy
“If a CBDC maintains personal balances on the ledger, which is a prerequisite for a retail CBDC, then privacy will become major challenge. (similar to the case digital banknotes.). While there are cryptographic systems for maintaining transaction privacy in such settings, they are complex and costly, and unlikely to scale to meet the requirements of a CBDC in the short-to-medium term. One critical observation is that pseudonymous accounts, i.e., accounts with holders names kept secret, offer only weak privacy. Under many circumstances, as the history of cryptocurrencies shows, it would be possible to deanonymize accounts. A CBDC will reveal significantly more information about individuals transactions to central banks than current systems do. This observation strongly motivates technical and legal confidentiality protections for ledger contents”.
Innovation
“The authors believe there is a wide range for innovation in a CBDC beyond mitigation of frictions in transaction processing. Some derive from the assumed transparency a CBDC would afford regulators, including providing overall but fine-grained view of economic spending. They include new monetary policy levers, like central banks’ ability to institute negative nominal interest rates, create currency with time-limits or other spending conditions, in order to create highly needed monetary interventions in a national economy. Novel financial technologies may be best captured with CBDC support for smart contracts, which can offer flexible means of defining policies. Others for the creation of new types of financial instruments; in cryptocurrency systems, they have led to the creation of instruments (flash loans) with direct analogs in the current financial system. Given the historically demonstrated hazards of smart contract bugs (The DAO), software assurance and oversight will have high importance”.
Secure hardware
“The authors recommend strongly thorough investigation of the utilization of secure hardware to enhance the security levels of the CBDC system. Even with vulnerabilities detected in recent secure hardware, that suggests not using them in critical subsystems. There are many other applications it can serve well as a fast helper to strengthen or harden the systems. The paper suggested an extensive set of solutions on utilization enhancing privacy through defense-in-depth protective layer, strengthening compliance enforcement by constraining the hardware system to operate only according to regulatory rules and protect the users.”
Two-layer architectures
“Most investigated designs focus on two-layer CBDC architectures. In such settings, existing non-governmental financial or payment application provider, (Payment Interface Providers or PIPs) [10] add a second layer over the CBDC, that would represent interface between users and the central bank. Two-layer designs accommodate and align existing customer service delivery and compliance mechanisms against money-laundering and illegal funding laws, this can transform the system smoothly without disturbing the existing operating banking system”.
“Two-layer systems may not solve the privacy concerns related to representing individuals’ accounts or banknotes in the CBDC. Tt may add complications. Like if to deploy smart contracts by PIPs, instead of managing them by the CBDC, each solution might bring with it hidden risks for control of regulators, synchronizing different PIPs’ deployments may prove incompatible, which would need a lot of adaptation interfaces to the CBDC. On the other hand, smart contract tight control environments by the central bank can cripple innovation. setting core technical and operating standards by the could prove a useful middle solution. The benefits and risks of CBDC are complex, correlations between financial, legal, and technical considerations. Nations do not have to work on a preset rules but should consider their own conditions and environments when they design their own settings before introducing a CBDC to compare benefits vs. liabilities”.
II.2 Our Evaluation and Comments on the Article
We found the article more to the point in addressing the technical and management issues. Risks and benefits were presented evenly. The model structure is presented as a case study itself. The article is long to cover fully. Hence, we have outlined matters related to justifications in the this section as a summary of potential benefits and risks. Then we started from section 2 of the article to describe the proposed model with all technical, management, legal and possible extension points of view. References in [brackets] have the same numbers as the original article. References are listed at the end. Referrals of the form (x.y, e.g. 9.1) are to section number in the article.
On justification of using CBDC, they count services that can run better by the current system. The CBDC provides the same core services and suffers the same overhead as the paper currency. What is the advantage for the customer seems to be just more control of the central bank over the banks, which in turn will become more controlling to the customers. If the central bank is penetrated by a group of big banks, the system may end up just under the control of monopolies, and the government becomes the server to give legitimacy (article section 2.0).
Implications for the international monetary system. It seems more control of the central banks is considered a default. More control is not reassuring (article section 2.2).
In relation to Identity verification, in fact a combination of personal identity and cryptographic online processing seem to be the best solution for the digital world identity problem, provided no single authority controls access beyond certain limits (article section 4.2).
The best wallet design for CBDC could work with cryptography processing connected to possible identity verification and tracking supported by the central system (section 5.0). Transaction and identity authentication are possible to handle, but for many users this is a big issue (5.1, 5.2).
Privacy, decentralization, and compliance. The PIP (Payment Interface Providers) can disclose the identity of an account under suspicion, where trust in the central bank is assumed. How they describe the central bank enforcement of compliance creates problems regarding the principle of using the CBDC (6.3, 6.4).
Secure hardware with built in cryptographic protocols is more powerful than each separately (8.5).Implementing monetary policy. Serious points are discussed with ease, where the central bank can add or remove to the balances of people by government mandates. If the states have the means to force their will on people, They will do. This may eraser people accounts by a click. With no means of cash, that puts the people and the economy under the mercy of a group with no justification (9.1).
CBDC designs and conclusions are model dependent, and how the CBDC is introduced into the economy. Sure, that would make a big difference (9.3).
CBDC Jurisdiction based on national entities. That is the assumption. “But there are certainly enough interconnections and global orders that would like to see a universal CBDC governing the world monetary system. Due to power influences of strong currencies like the US dollar on other world economies, some planners think a universal CBDC can replace the $US and all other currencies following the example of the Euro, which replaced most Europe currencies. In that sense it is not reasonable to ignore the evolution path when evaluating the realization of the CBDC experiment (10.1).
Centralization of a single transactional ledger enhances monitoring and makes the CBDC unattractive for money laundering. That applies equally to legal activities when people feel their assets can be arbitrarily seized. That also applies for other legal rights like privacy (10.2).
Libra association having the resources to disseminate its technology across national borders, and influence how digital money is spent globally. That strength and extensiveness without reference to an elected authority raises concerns more than assurances. Libra seems to represent a global power that can define the outcome of national central banks. It looks as an ideal Global multinational monopoly acting across national lines (11.1).
Libra looks more of exchange service basically than a true cybercurrency. The cypher part is to allow entrance across national lines without major legal responsibilities, while having the cryptocurrency minimum protection assurances from error correction and accountability (11.1).
Basing their future work on an ultimate issuance of CBDC by world central banks. Libra hopes to integrate them directly into the Libra network, and that makes a model for a world central bank albeit voluntarily and with no legal liabilities (11.1).
≋LBR and Libra stablecoins conversion to fiat currency will be handled by third party financial institutions called VASPs (Virtual Asset Service Providers), who will interact with end users. The paper design proposal seems to barrow heavily from Libra model (11.1)
The Digital Yuan nature is different from the Libra because it is a national project representing well defined geographical jurisdiction and objectives that can be backed by a well-defined legal system. Their ability to penetrate and control the rest of the world is not similar to the Libra experiment (11.1, 11.2).
The digital yuan users enjoy some degree of anonymity with respect to other users and banks. However, the have mechanisms to deanonymize suspicious transactions, in order to combat money laundering, and that can apply to any level of control they see fit. (11.2).
III. Evaluation and CBDC Comparison with Other Currency Representations
According to the two reviewed article, it seems the CBDC is the ultimate salvation. But it is not clear whose salvation it would address. Does the magical solution to money stability serve the public interest at large or the controllers as the beneficiaries. In that sense it is not easy to take the two article conclusions as a bible for economic solutions. At best we can highlight their technical advantages for certain financial functionaries, but at worse they can bring problems to the world economic system and social balance. In the following we outline prose and the counter positions as summarized by the article and other relevant conclusions.
III.1 Design of CBDC and Impact on Economic and Social Indicators
Table 1: shows the design parameters of the CBDC choices as envisioned by the article. There are certainly ranges of settings, and we used the most probable ones.
Table 1: CDBC design parameters and implications as envisioned by the article
| Parameter | Settings |
| Currency | Digital with no other coverage ensured store of value. |
| Ledger & distribution | Central to semi-central. |
| Types of operations | Standard financial management and retail markets. |
| Public access | Two-tire or direct. |
| Compliance | Strict control and implementation. |
| Privacy | Ensure full access to all information whenever needed. |
| Transparency | Arbitrary and as the law allows. |
| Technologies | Cryptotechnology is hard to reconcile due to weak control or reliability for a central system. |
| Novel solutions | Limited. |
| Hardware security | Not critical. |
| Highest risk and threat | Easy transformation to serve monopolies instead of the public. |
Table 2: Impact of using CBDC digital currency as the only way of money exchange as defined in Table 1:
| Issue | Advantages | Drawbacks |
| Stability | Could be enforced. | Hard and arbitrary control. |
| Credit availability | Can issue as much as needed. | Hard to cover such super fiat currency. Breakdown can be periodical with faster pace. |
| Privacy | Weak privacy and strong control by the central authority. | No personal privacy, and high possibility of abuse. |
| Transparency | As much as the managers want. | Possible too much exposure of individuals. |
| Compliance | Possible on customers, hard on the authority. | Power abuse and monopolies. |
| Control | Ultimate. | Possible financial tyranny. |
| Distribution and Centralization | Hard to implement decentralized; more like centralize with two-tire format. | The loss of semi centralization in direct central bank dealing with the public removes many possible innovations. |
| Risk control | Can as long as the economy performs well. | Breakdowns if the economy suffers. |
III.2 Potential Successes and Failures
Even if we accept the premise of the ideal benefits of the CBDC, we still cannot predict with confidence what are the success potentials. If we add the built in erroneous presumptions, we expect major deviations from the predicted modeling proposed and the article assertion of success.
Table 3: The potential failures for the design specs of Table 1:
| Issue | Success model standards | Failures |
| Stability | Hard without universal central CBDC. | Fragile for small economies. |
| Credit availability | Easy for central. | Easy breakdowns. |
| Privacy | Minimum. | Possible abuses. |
| Transparency | As the managers want. | Abuse. |
| Control | Ultimate. | Complete breakdown. |
| Risk control | Manipulative. | Breakdowns. |
III.3 Comparison With Paper Currency or Connection to Metals and Gold
This section compares briefly the various forms of currencies cost and benefits in a tabular way. We can see each form has its advantages. What we would like to see is a design of the CBDC that does not reduce the past currencies advantages while gaining the possible unique benefits of the CBDC. It seems however there are no unique benefits for the consumers, but there are ones for the management and the states. Table 4: shows the cost and benefits of various forms of currencies as paper note, and metals like gold and silver. We introduces here the comparison with CBDC.
Table 4: A comparison between paper notes, other traditional forms, and the (CBDC of Table1)
| Issue | Paper notes | Metals | Productive sector output | CBDC |
| Feasibility | Tested | Long history test | Very powerful indicator | Hard to predict |
| Soundness | 50/50 | True | True | Can be if the objective is to truly serve the economy |
| Stability | 50-50 | Full but hard to attain coverage | Works well with metals and digital processing of operations | Hard to envision without full control of the economy |
| Control | Least | Solid independence and reliability | Complex but most representative | Ultimate |
| Breakdowns | 50-50 | No, but shortage of metals | Only if the economy is truly breaking due to mega disasters | Very easy. The system is volatile if it breaks |
| Universality | Not feasible albeit tried | Natural to be | Natural to be | Will not work as envisioned by designed without it |
| Relation to the political System governing the world | Semi-Neutral | Strong | Representative | Simple form of central government authority |
| Effect on the productive sector and financial stability | Varies | stabilization | True action | Can manipulate it in un seen ways |
| Effect on social freedom & human privacy | Moderate | Positive but sometimes crippling due to shortage of metals for the public | A lively economy is the best for the freedoms | Ultimate interference |
| Impact on the nature of the human society form | Moderate | Hard to manage by the public | True interactive | Removal of the human factor and dominance of cold economics and machines |
III.4 Conclusions and Recommendations
- It is hard to design a reliable CBDC system without strong control. But strong control brings serious problems.
- Technical development can all serve the digital utilization of money without having to be all digital.
- Other currency forms besides notes can strengthen the economy reliability and reduce exchange rates fluctuation.
- Monopolies are the strongest detriment of economies and currencies stabilities.
- Smart contracts and cryptography methods are very useful in providing high levels of privacy, but they should still have a central reference with minimum authority control for legal protection.
- The best design are to provide cryptographic solutions in connection with privacy and freedom, but with features that can track under limited conditions with complexity of execution and level of authorization.
- Other notes and comments in the work analysis shed light on more details.
- Recommendation: keep digital activity, but do not enact CBDCs.
IV. Detailed Review
Article: Design Choices for Central Bank Digital Currency Policy and Technical Considerations
Our review of this extensive article: we found it more to the point in addressing the technical and management issues. Risk and benefits were presented evenly. The structure of the model is presented as a case study itself. The article is too long to fully cover. Hence, we will pass by all issues related to the justifications where we put them in the first section as a summary of potential benefits and risks. Then we start from section 2 to describe the proposed model with all technical, management, legal and possibly extension points of view. Reference number in [] have the same number as the original article. The other references are listed in the end
1. Introduction
1.1 Interest and potential adoption of CDBC
- Over 80% of central bank respondents to a Bank for International Settlements survey in 2019 reported engagement in CBDC projects [1]. 10% of these banks, representing 20% of the world’s population, envision they would offer CBDCs within three years. The People’s Bank of China has begun to pilot a digital yuan [2].
- Hearings on CBDC took place in the U.S. House Committee on Financial Services [3].
- The European Central Bank has initiated a project to explore CBDC development [4].
- Sweden is testing a CBDC e-krona [5].
- Facebook-initiated fiat-backed cryptocurrency Libra offered prospect of an industry alternative. Regulator concerns about the project [6] and speculation it has catalyzed CBDC development [7] highlight Libra’s relation with CBDC.
- Various forms of CBDC have existed for years, but available exclusively to financial institutions [8].
- The most potentially decisive change is to apply CBDC to retail and allowing individuals consumers to have central bank accounts.
1.2 Focus is on retail CBDCs.
The paper discusses and evaluates the design choices, mainly technical, but also financial and legal, that central banks will encounter in their exploration of CBDCs. Contributing authors include experts in computer science, economics, and law with practical experience in the design of digital currencies. The paper emphasizes choices, and challenges that will define CBDC deployment or realization. Both cryptocurrencies and CBDC offer evidence of feasibility for retail deployment of digital currency. The technical basis of Libra have influenced CBDC design plans, and the article recommendations.
1.3 Benefits and risks of using CBDC
Benefits: the authors summarize the benefits in the following, but not all people would consider them benefits
- Efficiency: can reduce friction payment systems, by reducing monetary cost and increasing the speed of transactions finalization.
- Broader tax base: add more economic activity into the tax net, boost revenues and limit tax evasion.
- Flexible monetary policy: The zero lower-bound constraint on monetary policy set by the banks can be relaxed,
- Payment backstop: to private sector managed payment systems, avoiding their breakdown during crisis of confidence and rise in risk.
- Financial inclusion: can provide options for unbanked or underbanked individuals to have access to electronic payment systems, and products and services.
- Opportunities for novel financial technologies, particularly for regulators.
Risks: the above presumed benefits should be tested against potential financial and technical risks. They include:
- Disintermediation of the banking system: the removal of an intermediary in the supply chain by reducing transaction frictions and possibly even providing interest- bearing accounts [8], Still many CBDC designs seem inclined toward a two-layer architecture with the CBDC as the core player, while non-governmental financial institutions manage a second layer that deals with users.
- Miscalibration of government involvement: Two- layer architecture offer financial institutions chance to innovate on top of a CBDC [10]. A CBDC connected to a central bank activity that can efficiently be managed by the private sector could limit innovation. But bankers’ systemic risks and incompatibilities can rise without central bank involvement.
- Risks due to lack of regulatory expertise and capacity: With increased speed and efficiency come new risks, financial and technical. Regulators may develop tools and expertise to address these risks in the face of a change in the basic operation of the system.
- Loss of privacy: given the complexity and limitations of current privacy protection technologies, it seems likely a retail CBDC will expose new forms of sensitive information to operators. CBDC designers should consider legal and technical mitigations.
- Technological vulnerabilities or design mistakes: CBDCs will represent a technical experiment, whose risks of information security failures and fundamental design mistakes should not be underestimated.
1.4 Core functionality
The core of a digital currency is a digital record of all transactions that have occurred in the system. That is called a digital ledger, which is a digital bulletin board where all transactions in the system are posted. The transactions in the ledger determine the account balances. The set of all account balances at an instance is called the state of the ledger. To remove ambiguity in the balances at an instant, the ledger must also record transactions sequence generally based on their time of receipt.
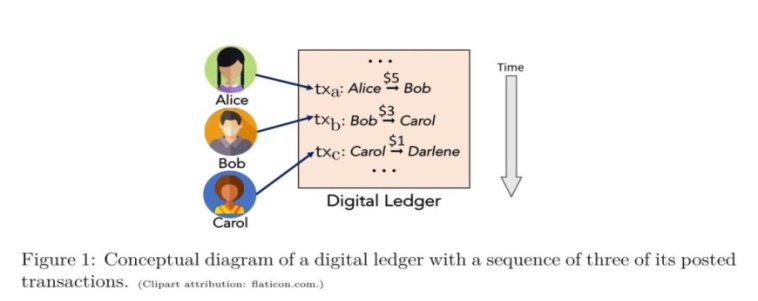
Figure 1: Conceptual diagram of a digital ledger with a sequence of three posted transactions.
In the view of a ledger new transactions are appended and creating continually growing ordered transaction list. Figure 1.1 shows a conceptual diagram. A ledger may be thought of as a database with an append-only structure, i.e., in which no transactions are deleted. Most databases, however, allow records to be deleted, and are thus not digital ledgers in sense that the term is currently used. Despite their weaker data integrity assurances, they could be used to realize a CBDC.
2. Banking Perspective
The specific innovation considered in the paper is the replacement of central bank issued money that can be used for retail transactions with their digital counterparts. CBDC are fiat currencies issued by central banks in digital form as a replacement of physical currency. A simple form of CBDC is e-money. Another option is that all agents of an economy can access central bank accounts, that can be interest-bearing. In such setting the central bank becomes the manager of payments system depending on the CBDC structure. The e-money is easiest to implement and in combination with mobile phones it has potential to improve financial coverage and reduce dependence on cash dependence. The retails application is complicated but has a potential of scaling up into a payment system that serves as a backup to the private payments infrastructure.
One concern about central bank deposit accounts is the possible disintermediation of the banking system. Recognizing this risk, some central banks are taking a hybrid two-tier approach where they disseminate CBDC to commercial banks, just as they do with cash. Here commercial banks distribute them to customers by setting up and managing digital wallets. [So they provide the same services and suffer the same overhead as the paper currency. What is the advantage for the customer is more control of the central bank over the banks which in turn will become more controlling the customers. When the central bank is owned by a monopoly of some big banks the system end up just under the control of the monopolies and the government becomes the server to give legitimacy 2.0].
2.1 Technical definition
There is no clear consensus on the CBDC definition, with both conceptual and technological issues still under development. Both issues are tied to a motivation for central banks to issue a CBDC. The following is used: Kumhof and Noone [11] define CBDC as “electronic central bank money that: (i) can be accessed more broadly than reserves, (ii) has functionality for retail transactions, (iii) can be interest bearing (with a rate different from that on reserves), and (iv) has a separate operational structure relative to other forms of central bank money”.
2.2 Implications for the international monetary system
One of the major benefits of improved electronic payment and settlement systems based on digital currencies is the speed and security of transactions, and costs reduction. This can make significant improvement for settlement of trade-related transactions. Even cross-border settlement of other types of financial transactions could benefit from these developments. DLTs may offer reliable tracking of different stages of trade and financial transactions, reducing associated frictions.Both banks and nonbank institutions could expand the geographical scope of their operations across national borders using the new technologies. This creates new challenges for supervision and regulation. One complication is the lack of clarity about the domicile of informal financial institutions and the geographical locus of the supervisory authority of national regulators. The second is the potential accentuation of cross-border financial stability risks as more institutions operate across national borders. Some of these problems can be addressed if conducted using a public DLT or if the regulator has access to the relevant private ledgers. [More control 2.2].
The expansion for efficient cross-border financial flows could end up problematic, It speeds their integration into global financial markets at the risk of higher capital flow and exchange rate volatility, which often causes significant stresses for corporate and sovereign balance sheets in economies. These issues can increase if new payments systems and digital currencies increase both the volume and fluctuations in cross-border flows reducing capital controls and adding to volatility. The intensification of global financial cycles could also constrain monetary policy independence, even for central banks that practice inflation targeting backed up by flexible exchange rates. New channels for transmitting payments quickly are likely to make it difficult to regulate and control capital flows.
3. Ledger Infrastructure
Current digital currency systems maintain a global state, comprising the balances of users. This includes banks’ per-client balance tables to cryptocurrencies like Bitcoin [17] and Ethereum [18]. Transactions are updates to the state They can transfer funds or interact with smart contracts. The transactions are serialized in a single ledger. The state is the result of processing the transactions according to their order. They are aggregated into blocks, that are linked to form blockchains (Figure 2).
The system allows participants to add blocks in a serial order, and it evolves deterministically. It also allows only transactions that abide by its predefined rules, and prevent the removal of a block, which would have implied a reversal of history. To avoid vulnerability to crash or misbehavior, the blocks and state replicated, and processed concurrently by multiple machines. To orchestrate the replicas so they all agree on this order and behave like a single coherent machine, despite network latencies and arbitrary misbehavior by some of them. This is called State Machine Replication (SMR). Due to distributed formats or hardware failures, it is important to incorporate multiple nodes for fault tolerance.
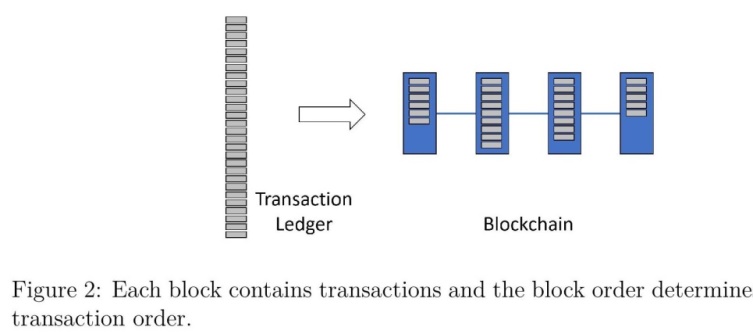
Figure 2: Transactions and the block order determines the global transaction order.
Design of the SMR and networking layers affects the system performance and security, but significantly defines how the system is decentralized. This choice determines how open the system, and how much it controls entities, to redefine behavior, halt operation, or withhold certain transactions. Decentralization designs, vary from balance tables, semi-centralized systems like Ripple [19] and Libra [20], to cryptocurrencies, and trade-offs considerations when designing a CBDC. In order to accommodate the CBDC, the system should process a large number of transactions in a short time. Scaling ledgers to large transaction volumes include system state sharding or partitioning.
3.1 Confidentiality, Integrity, Availability
A digital currency must satisfy core security properties. namely, confidentiality, integrity, and availability as in shown in Figure 3. Confidentiality means no leak of information. Integrity means information be always correct and produces correct results to computations. Availability means responding promptly and retrieving only the requested data or operations, such as committing a digital currency transaction. To ensure all that, techniques for distribution and decentralization, fundamental to cryptocurrencies and CBDCs are needed
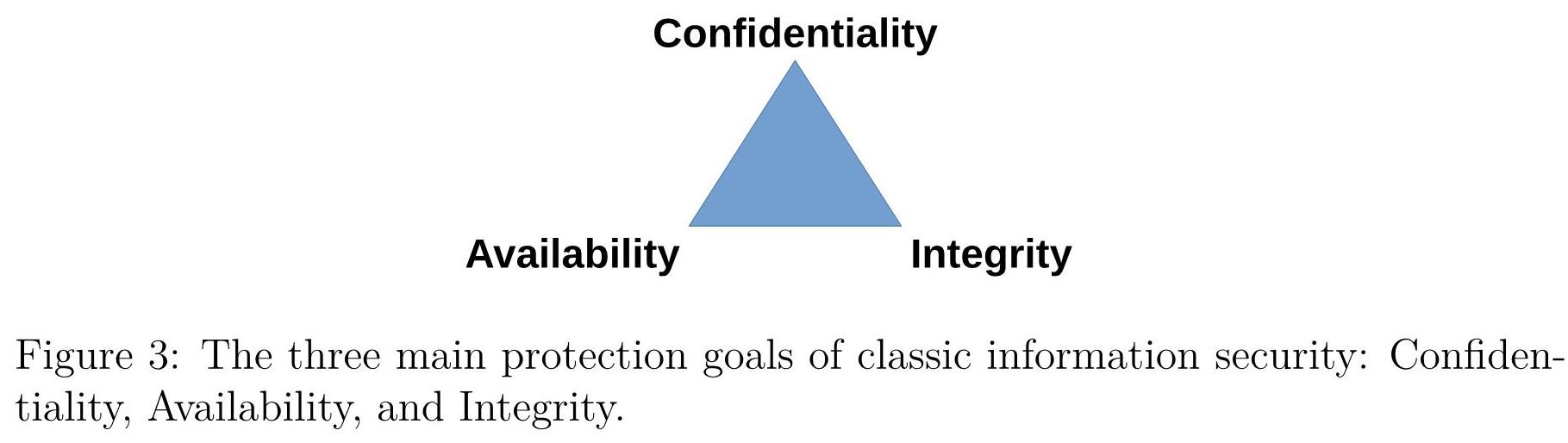
Figure 3: The three protections of classic information security: Confidentiality, Availability, and Integrity.
3.2 Distribution and decentralization
Distributed systems: consist of multiple devices communicating and coordinating over a network. The most relevant system for a CBDC is a distributed ledger. Using state-machine replication or consensus algorithms the devices making a digital ledger maintain synchronized copies of the transaction history. Geographically distributed systems, distribute the replicas in different cities or regions, so power outage or network failure does not kill the entire service. Cloud infrastructure is highly centralized by being owned and controlled by one authority.
Decentralized systems: is a distributed system whose composite devices are not under control of a single, central authority. Decentralizing in principle reduces the amount of trust we can place in components, but also limits the damage any single authority can cause if compromised. Decentralization refers to role separation, trust dispersal, and/or threshold trust.
Role separation: is the weakest form of decentralization by dividing a process into qualitatively-different functions carried out by multiple authorities serving in different roles.
Trust dispersal: when a role in a distributed system is played by independent authorities, but each serving only a small part of the dataset, trust is dispersed among these authorities. The dispersal of governmental powers across regions is a classic example. When companies implement the PIP role on behalf of their customers, they need to trust it. The aggregate trust of the entire system is dispersed among the firms serving that role.
Threshold trust: users individually or collectively split their trust across several authorities independently, so that no single authority or small coalition have unlimited power or authority over any user. A board of directors or parliament is a classic organizational embodiment of threshold trust, A distributed ledger, spread across a consensus group of servers operated by independent companies provides threshold trust in terms of the ledger’s availability, so it remains available to all users even if anyone or a limited number of member servers leave.
3.3 State machine replication SMR for distributed ledgers
The level of decentralization of the ledger state-machine-replication can be roughly divided into three categories.
Centralized ledgers: the central bank runs the system itself. This is the easiest to manage and builds on classical system design. However, this design misses some central goals of a CBDC which can unilaterally withhold transactions or even change the rules or revert history. The users are not getting the same guarantees as in cash. These aspects are similar to payment application. History revision should be prevented by ensuring that transactions are irrevocably committed in centralized but verifiable ledgers, but one can do better.
Fully-centralized design where the choice of nodes and their operation is under direct control of one authority. Such central control can potentially change the rules at will, roll back system state or rewrite history, and censor or delay transactions. These capabilities may be desirable from management perspective, but they are not desired by robustness or public trust. Figure 4 shows how to deal with untrusted data-store
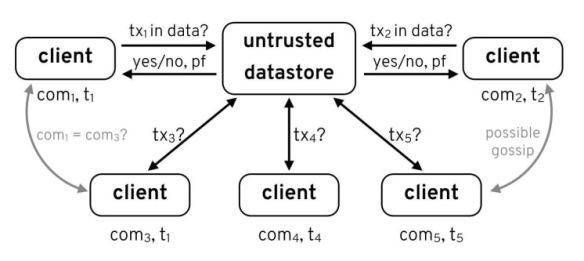
Figure 4: An overview of the interactions involved in an authenticated data structure. Clients do not trust the server. When the server tells a client whether or not a transaction is in the dataset, it provides a proof of that, which the client can check against a commitment to the data it maintains and updates when needed. To ensure the server has a consistent view of the dataset to all clients, a form of gossip is needed. The example on the left, clients with commitments representing the same point in time (𝑡1) may want to check that these commitments are identical.
Centralized but verifiable ledgers: there are still ways to limit the trust that clients need to place in the servers maintaining the ledger. Authenticated data structures [31]–[34] (ADSs) provide a method where a server, in possession of some data, can prove things about that data to a client who does not necessarily trust the server to give accurate answers. A client receiving money in a CBDC may want to ensure that the transaction has gone through before providing any goods or service; i.e., they want to check for the inclusion of the transaction in the ledger. In an ADS the server provides a cryptographic proof of inclusion that the client can verify.
Table 5: Centralized vs. Decentralized Infrastructure.
| Centralized | Semi Decentralized | Decentralized | |
| Case Example | Amazon Ledger Database [21] | Libra [20] | Bitcoin [17] |
| Performance | Excellent, full control of infrastructure | Good, SMR with many participants] |
Challenging, active area of research |
| Censorship | Easy: single operator | Possible: particularly if operators are in the same jurisdiction |
Hard: operators might not even be identified |
| Rewind | Easy: can be done quickly by single operator |
Hard: takes longer for operators to agree, implying longer history to revert and worse violation | Extremely hard: requires cooperation by majority of possibly unidentified operators |
Semi-centralized ledgers: To reduce centralization, the CBDC can instead be operated by a larger set of independent parties chosen or approved by the central bank. Superficially, the solution is similar to the centralized approach instead of directly operating the nodes, the central bank chooses the entities that run them.
A decentralized system implements an infrastructure similar to cryptocurrencies–The decentralized option implies a lack of centralized control; which could be the goal of a CBDC, but due to legal and regulatory considerations it is not acceptable in the CBDC context. Table 5: compares and summarizes these choices.
3.4 Scalability to large transaction volumes
How to scale performance beyond the capacity of a single server. A fully decentralized architecture has protocols that allow for high transaction throughput. Still all those transactions must be processed, and the workload can grow beyond the capacity of any one server. The openness of permissionless systems do not not help the system handle increased transaction load, because each miner replicates. All need to process all transactions, hence the maximum processing rate is fixed.
Complementary solutions include [76], [77] split the state into multiple parallel ledgers. Each ledger is operated by different servers, allowing the system capacity to grow by the number of parallel chains. Care must be taken when to make sure the security of each chain does not deteriorate compared to a single chain. [78] operates a ledger with some arbitrary protocol but replace with several interconnected servers that operate as a single high-performance node. This solution keeps security properties of the original protocol and allows for scaling of resources available to the different nodes.
4. Account and Identity Management
Since a CBDC cannot achieve its maximum usefulness unless ordinary individuals can hold and use the digital currency, this raises the key question of who should be responsible for managing accounts and answering associated responsibilities such as identity-checking for know Your Customer (KYC) compliance.
4.1 Who manages accounts
Central banks traditionally do not have relationships with individuals, they effectively delegate managing personal accounts to banks.
Direct personal accounts at CBDC is new business, bringing new challenges and risks. personal accounts with the central banks may concern citizens as well: Many potential customers can be inclined to entrust their financial information to a local business than to a remote government agency do not regularly interact with directly.
Accounts in cryptocurrencies: are designed to deal with the identity management problem by defining accounts in terms of cryptographic keys. These accounts are strings that represent cryptographic public keys. They are available to any person who knows the private key associated with that account can spend the currency it holds. These decentralized cryptocurrencies look like cash but have with them the risk of simple hacking or even removal.
Cryptocurrency exchanges: to bridge the gap between the keys and human identities created centralized exchanges The exchange allows trading traditional currencies cryptocurrencies. That needs creating traditional accounts and business relationship, directly or delegate the identity-checking tasks required to ensure legal compliance. Exchanges make cryptocurrency seem more convenient, legitimate and compliant. But in reality most exchanges are centralized third parties that must be trusted with the custody of users’ cryptocurrency balances, bringing all trust related problems including corruption or external hacking. The problem is not the original solution of combining encryption with identity but the delegation to ever increasing trust monopolies.
Delegated CBDC account management: may be natural for a CBDC to delegate this task similarly. This is a key requirement by the Payment Interface Providers (PIPs) in the Bank of England’s CBDC proposal [10]. It seems reasonable. The Digital Yuan also is adopting this model. Negative aspects include adding more power and ease of monopoly by the banks or the central banks, without any true advantages to customers, while reducing their cash freedoms. The authors claim it brings also a limitation to innovation. By the central bank or the banks.
4.2 Identity verification
This is fundamental problem that no digital technology can solve with complete security. What we have is a plethora of procedures for associating accounts with imperfect proxies for individuals.
Physical-world credentials include ID cards and passports, biometric templates, or interconnections in a social trust network. Some work better than others, but all have problems in failure modes. This is an inherited problem with all digital solutions. The authors outline the following possible solutions while admitting they all have problems.
In-person identity checking: requiring the customer to present a government-issued ID or passport often with other evidence such as utility bills, in order to open an account. This needs financial institutions with local branches willingness play the role of PIPs for a CBDC, with digitization trend this may not prove feasible. Still not true alternative exist.
Online identity checking: many companies have started offering online video identification services, asking for suitable forms of traditional ID over a video chat session. Using machine-learning and video face-recognition techniques [83], seem genuine and appears to match the face of the person holding it but in reality that can always be fooled. The algorithms must distinguish between an actual, live person and a static image or video recording of one that an identity thief might be using. This will never replace in person trust.
Weak digital identity proxies: such as E-mail addresses, phone numbers, IP addresses, or simply asking users to solve CAPTCHA puzzles [91], [96]. These weak identity proxies are not adequate, because they do not, reliably face the creation of false identities. Mobile phone numbers can be slightly stronger identity proxies, since many countries require customers to show ID when signing up for a calling plan, but anonymous prepaid plans still exist nevertheless. Most identity online proxies increase the cost of abuse somewhat without reliably protecting. Any hacked single registration device can be used to synthesize false biometric identities or impersonate real users. Most biometric templates previously thought to be irreversible have been proven otherwise [112], and cryptographic algorithms are not adopted because their complexity.
Self-sovereign identity allows institutions to assist with identity verification by issuing attestations, and in principle gives users control over how much personal information to reveal. They seem promising but there is no standard, and the technology is not mature to make it suitable for adoption by universal systems like the CBDC.
[In fact, a combination of personal identity and cryptographic online processing are the only solution for the digital world identity problem, provided there is no single authority that controls access beyond certain limits 4.2].
5. Digital Wallets
Digital wallets are applications through which users interact with a digital assets system, like currency. It enables users to view balances, make payments, receive, and trade digital assets or invoke financial transactions. Their design and operation are critical for security and privacy. Money-transfer apps Venmo or Alipay or banking services on mobiles can be considered digital wallets, These however, support user currency operation within the current financial infrastructure. They do not create new representations as CBDC, but they provide an approximate vision of the user experience that CBDC digital wallets need to offer to attract popular adoption.
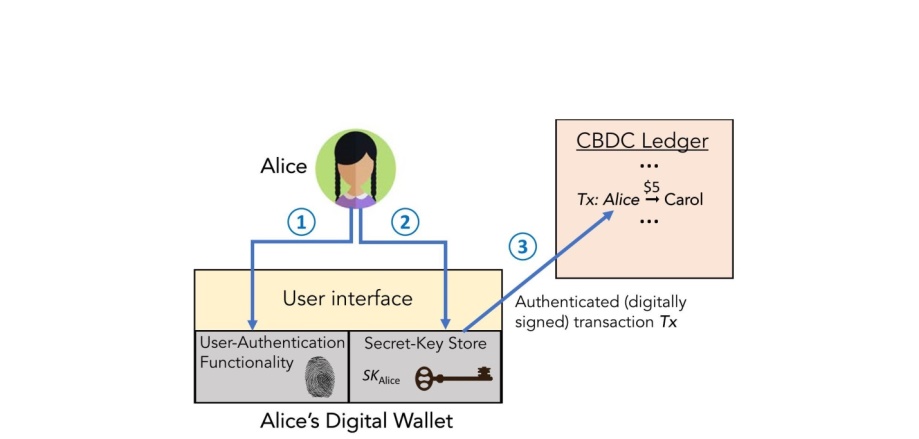
Figure 5: A digital wallet transaction workflow. User Alice sends $5 to another user, Carol. Alice interacts with the wallet through its user interface. She first authenticates herself to the wallet. She then instructs the wallet to send $5 to Carol, whom she identifies by means of an account number or username. Her wallet uses a secret key associated with Alice to digitally sign a transaction Tx specifying payment of $5 and sends Tx to the CBDC system for inclusion on the ledger
Wallets for decentralized cryptocurrencies are similar to money-transfer applications in terms user experience. But they differ in that the cryptographic keys authorizing fund transfer must be stored on the user device rather than being entrusted to other services. This makes their wallets more cash-like. The reliance on the wallet device instead of service provider presents similar cash like problems of hard to recover the lost or stolen assets. Driven by the security sensitivity they also come in special-purpose hardware formats that function differently and take advantage of the hardware security practices.
Digital wallets can play a role in managing a broad range of assets (cryptocurrency, digital tokens, smart contracts, digital cats [144]). Their capacity to hold different assets creates critical opportunities and risks as occurred by the ICO bubble enabled by Ethereum’s ERC-20 standard [145], [146]. The question of whether a CBDC is held or used via special designs, or generic wallets that can a wide range of assets, needs well studied investigation. Digital wallets have three functionalities: user & transaction authentication, and a user interface for transactions. Figure 5 shows the components and workflow of a digital wallet. [The best wallet for CBDC could work with cryptography processing connected to possible identity verification and tracking supported by the central system 5.0].
5.1 User authentication
Authentication must ensure that only the owner or his delegate can operate the wallet or access the currency. They use passwords for the purpose. With growing dependence on mobile systems, it is frequent to authenticate biometrically. The user can access the assets by running the wallets on their devices. User authentication overlaps with identity verification that can be a condition for wallet registration in many systems. After creation, securing the wallet requires it is accessed by the owner or his delegate). The wallet can be hosted by a custody service, taking the form of an account with a financial institution, and does not need access by a device or application. Custody services by owners of cryptocurrency do not afford direct access technical complexities.
5.2 Transaction authentication
A user can instruct the wallet to perform transactions on currency in his account. The wallet must create and send a transaction message 𝑇 to the CBDC system for inclusion on the CBDC’s digital ledger. the CBDC must ensure that authentically issued transaction. If Alice issues a transaction 𝑇 paying $5 to Bob, the system must ensure that Alice herself authorized 𝑇.
In banking user and transaction authentication are combined. If Alice performs user authentication and sends $5 to Bob, the bank can identify the transaction as valid because it has already authenticated Alice. The entity that authenticates the user is identical with the one that manages the money. A CBDC could operate the same way, requiring users to log in and perform transactions. In two layer CBDC an intermediary can submit transactions on behalf of users it has authenticated. Approaches of this kind has the benefit of conceptual and design simplicity. But they create a killing single point of compromise that is attractive hackers. Should the CBDC be able to confirm transactions unilaterally, then it would constitute a single point of compromise. Checks and balances are lost.
Design for cryptocurrencies transaction authentication requires they are in a cryptographically signed by the owner In such a design based CBDC, the wallets perform transaction authentication by digitally signing user initiated the transactions. They play the critical role of storing the user private keys. Such task (called key management) is a challenge in cryptocurrencies, providing enough lessons for similar CBDC designs.
Key management: An estimated 4M Bitcoin, worth tens of billions of dollars, have disappeared forever because of lost private keys [149]. Key management is so challenging for user they prefer to store cryptocurrency with exchanges such as Coin base, re-centralizing systems whose main selling point decentralization. Ideally, a digital wallet can be an app on a mobile device that secures a users’ private keys effectively and provides them for signing when needed. Problems arise if the mobile is lost or broken or hacked. [Such problems are simple to handle but for many users this is a big issue 5.2]. There is a conflict between security, and availability. Perfect security and availability can be ensured by posting the private key on a blockchain, but how can one trust the blockchain. The problem is making a balance between security and availability. Cryptocurrency world has developed methods for key management with mixed success:
Secure hardware: Most mobile devices contain secure elements, designed to store keys so that they can only be accessed upon successful user authentication. Hardware wallets in principle reduce the risk of funds loss due to remote compromise (e.g., hacking) of the device holding the wallet, but they do not by themselves mitigate the risk of funds loss through loss or destruction) of the wallet device. Trusted wallets hardware is discussed in section 8.4.
Mnemonic seeds: Users are encouraged to write down their mnemonic seeds and store them physically safely to enable simple recovery of lost private keys. This helps guard against loss of funds through loss of the device holding the information.
Threshold signing/multisig: by split a private key into a set of 𝑛 shares (section 3.2), any 𝑘 out of 𝑛 shares (for 𝑘 ≤ 𝑛) can reconstruct the private key. Advanced protocols [152], [153] enable generation of a signature from shares without explicit reconstruction. With such design, it is possible for 𝑛 different entities to exert joint control over a digital asset, with any 𝑘 having signing authority.
Cryptocurrency wallets: multisig transactions are popular. they are similar to threshold signing and have the goal of joint control. They require using 𝑘-out-of-𝑛 distinct signing keys to validate a transaction. Both threshold signing and multisig transactions representations of the threshold trust in decentralization (Section 3.2.) They both achieve a security and availability balance by parametrizing 𝑘 and 𝑛 and various other enhancements [154], [155]. A limitation they are not good for single users even though that can be built.
Key management in CBDCs: Key management hard in decentralized cryptocurrencies because there is no central authority to remedy failures such as key loss. Erroneous transactions are irreversible; and many users have suffered losses [50]. In CBDCs, or any permissioned currency system flexible key management regimes are possible.
5.3 User interfaces
The capabilities user interfaces are highly important to CBDC users. Because designs can profoundly impact users acceptance and system security. Hackers and researchers show how misguided graphical design choices have caused users to misinterpret browser content. Some have been vulnerable to attacks that cause them to navigate to unintended, malicious sites[156]. USB-type hardware wallets for cryptocurrencies try to Handel such problems. Many have features to prevent malicious subverting digital wallets through displaying deceptive cryptocurrency information to users and generate transactions that send money to attackers. These devices include built-in displays that show the true destination address for a transaction.
Users get limited benefit from these cues [157]. Fraud-control methods depend on some form of manual and/or automatic surveillance of transactions, however, but that infringes on privacy challenges. Some CBDC proposals, and CBDC-like systems like Libra, adopt the sovereign control of wallets by users. Unless the CBDC takes on the task of fraud detection and remediation like commercial banks, sovereign wallets need to follow strict security requirements like those in cryptocurrency platforms.
6. Privacy and Transparency
In permissionless and decentralized cryptocurrencies [17], there is minimum regulation or compliance. Such systems are designed not to be controlled by a central authority, but they are shadowy. A CBDC needs methods to enforce compliance. States need to stop violators to ensure stability [10], [159].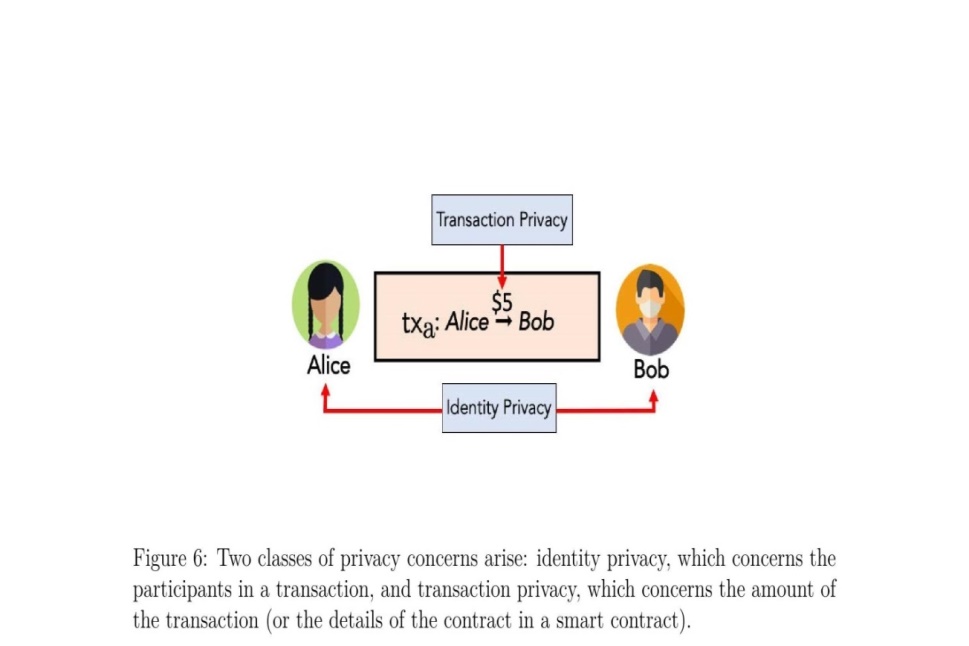
Figure 6: Two classes of privacy concerns: identity privacy concerns participants in a transaction, and transaction privacy, concerns the transaction amount or the smart contract details).
In one side CBDC transactions can use real identities visible to the central bank or law enforcement. Oversight and compliance would be easy. But oversight can bring abuses and human rights violations, enabling the government or banks to track individuals beyond limits. On the other side CBDC offers full privacy that would not reveal any information about transactions to the operators like cash. This can enable money laundering with no enforcement to track flows. A middle ground would be to offer some privacy protections while ensuring some visibility to auditors and law enforcement. The choice of such middle ground will reflect on human and cultural values. It is highly important for the CBDC identity-management approach to fit the cultural values of the user population. Moreover, choosing a middle ground depends on the technical tools.
Transparency is essential because validation demands ensuring transactions accuracy and compliance with rules, with more information to validators, which empowers them to learn about individual transactions and the people executing them with some potential abuse. This conflict does remove the need of both. Privacy protection technologies can achieve privacy and transparency in different forms Two privacy types a digital currency should consider (Figure 6). Identity privacy (Section 6.1) describes the ability or not to link transactions to their sender or recipient. For example, we may wish to prevent an observer from learning that Alice sent money on Tuesday. Transaction privacy (Section 6.2) describes the ability or not to learn the transaction content. This privacy requires different tools. The correlations between identity and transaction privacy have implications for decentralization of a CBDC (Section 6.3) and compliance (Section 6.4).
6.1 Identity privacy
Payment system can try to keep users’ anonymity by using pseudonyms. In practice pseudonyms can leak information about the participants in the transaction. Blockchain analytics companies’ entire business model is centered on de-anonymizing users (Chainalysis [160]). In Bitcoin, pseudonyms are clustered according to patterns [161]–[164]. An exchange can combine the addresses of different users to enable identification they are from the same exchange.
Solutions: two approaches the face these attacks. One is to remove pseudonymous identifiers. Cryptographic methods ensure that any two transactions by the same user cannot be linked via the transaction contents but can still be validated [168]. This increases complexity of use but makes it much harder for adversaries to link a user to his transactions. Without pseudonyms it is still possible to link individual transactions to an IP address. A common remedy is to alter the relay dynamics. Users may route transactions through proxies using third-party services such as Tor [169]. However, this solution is not scalable nor usable by average users due to high technical complexity. In addition, it requires users to trust a third-party service which is a problem on its own. In general, there are no cryptocurrencies or privacy features today fully prevent attackers from getting information about senders and recipients’ identities. This means the ledger of a CBDC visibility is not desirable,
“A better ledger design is not to require active active privacy exchange with anyone to find if a transaction is added to the ledger. In the SkipChain structure [173], [174], all committed blocks are collectively signed by a rotating committee, whose evolution is validated by collectively-signed forward links. This structure enables clients to provide a direct cryptographic proof of a transaction commitment to the ledger, without revealing privacy sensitive queries to nodes or other third parties. Complexity and security trade-offs must be used. The Libra blockchain has adopted it [175] and some variants may fit for CBDCs”.
6.2 Transaction privacy
Other aspects of blockchain computations users may want to hide the amount of the input data. In a smart contract, this can include metadata. In addition, users sometimes want to hide a smart contract content. For example, participants want to run a private algorithm for estimating the loan viability, without revealing the algorithm structure. Data privacy and program privacy problems are handled by different methods.
Data privacy: The simplest form is hiding the amount. This needs advanced cryptographics, such as encryption or commitments. The amount can be hidden using encryption, but validators must be able to check the applicability of the amount even without knowing the amount themselves. Cryptographic primitives known as zero-knowledge can provide proofs that the amount they are sending does not exceed their current balance. These proofs take longer to generate and verify than a regular transaction (a significant concern is that validators likely want more than this level of verifiability, in order to ensure compliance with financial regulations. Another limitation of zero-knowledge proofs is that they can only prove facts about confidential data held off the ledger but cannot ensure that the data is actually retained or disclosed when policy requires, as determined by a regulatory process or a smart contract.
Program privacy: Generalizing to smart contracts is hard for two reasons. First, the inputs to a smart contract can be more complex than regular transaction. Second, the operations executed in smart contracts are more complex. These issues make it difficult to extend zero-knowledge proof techniques for verifying encrypted transactions to arbitrary smart contracts. A solution is using secure multiparty computation (SMC), which is a class method that allow parties to compute encrypted data function without learning its inputs. Although SMC is generally inefficient, recent efforts have modified industrial blockchains like Hyperledger Fabric to support a class of SMC smart contracts optimized for performance [178].
6.3 Privacy and decentralization
One of the central questions is what the CBDC’s threat model should be for privacy purposes: i.e., from whom should the CBDC protect sensitive identity and/or transaction data? If it is acceptable from a social, legal, and risk perspective to require users to trust the central bank to protect their privacy, then a fully centralized design may be the most effective at protecting clients from each other. In such a design, however, a single bulk data breach of just one replica of the ledger or database can expose the identities and financial histories of millions of users, as the Equifax breach affecting nearly half the US adult population amply demonstrated [182]. Advocates promote more decentralized solutions to privacy protection, which a CBDC design should consider. The three main forms of decentralization (Section 3.2) are useful to for user privacy against the abuse of one server or authority.
If central banks treat accounts as pseudonymous public keys, and only the PIPs who will verify and record the identity information, then individuals are pseudonymous for the central bank and the ledger transactions provided. The PIP protects this identity information reasonably. [The PIP can disclose the identity of an account under suspicion. Trust of the central bank is assumed 6.3 ].
6.4 Privacy and compliance
Compliance goal is to protect the economy against malicious activities like money laundering or tax evasion. If a central bank deploys a CBDC, most likely it would want to detect or prevent large transactions that exceed the limits CBDC might introduce and enforce new compliance rules to protect financial stability. In crises people are worried about their banks and they may want to deposit into CBDC This can make the risk of bank run more probable. The resulting flight of funds might threaten the whole system stability. Solutions suggest capping how much CBDC any individual can hold. Such limit is a new enforcement that might be used [This is a big worry for all aspects of using the CBDC 6.4].
Challenges: Recent research efforts have explored the question of how to combine anonymous payments with compliance and oversight. In the context of token-based digital currencies, Camenisch et al. designed a solution that for users to make payments anonymously but the bank who issued the coins can enforce compliance policies by applying limits [186]. The main problem with such solutions is that they do not provide recipient anonymity or hide payment amounts.
7. Smart Contracts
Smart contracts arise from the need to extend spending limits and policies provided by digital assets. Many digital assets feature a smart contract language. This is a how independent development can extend with new tasks. It is not necessary for CBDC to utilize smart contracts to meet its role as a digital currency, and some CBDCs (digital yuan) are not going that path. However, they can provide how a CBDC can facilitate innovation from other entities like banks and financial technology providers. There are many designs using smart contracts for a CBDC to pursue, and possibly many benefits. Many costly losses in cryptocurrencies like Ethereum occurred due to smart contract coding errors. This resulted in accidental losses or became vulnerable to hackers attacks. If a CBDC incorporates smart con- tract functions, they should consider safety and security when designing.
7.1 Balancing between safety and extensibility
The need for program verification: Even in Ethereum’s first few years of operation, numerous expensive disasters were caused in part by smart contract errors introduced when developing the smart contract programs. These have underscored the importance of program verification and other verification tools that can help identify such errors or correct them. Three cases are instructive for showing potential solutions: the 2016 theft of $50M USD worth of Ether from “The DAO” smart contract, the July 2017 theft of $30M USD worth of Ether from the Parity Wallet smart contract,12 and the November 2017 accidental loss of $30M USD worth of Ether from the same Parity Wallet smart contract. In all of these incidents, the underlying programming errors were subtle and were not found during security audits and code reviews. In the first two incidents, the vulnerabilities were deliberately exploited by hackers who aimed to profit from the theft, while in the third case the loss was triggered by accident — the funds were not stolen, they were simply made inaccessible. A CBDC should take efforts to prevent such disasters with forethought.
Verification and analysis: A CBDC can prevent smart contracts errors by developing analysis tools integrated with their system. CBDC must select the best smart contract technologies and should count these tools’ reliability. They may put mandatory rules for some program analysis, which can be enforced automatically.
Domain-specific languages: Capabilities expected by the CBDC designers can be hardwired. This prevents bugs corrupting smart contracts but can foreclose on innovations. Many current smart contracts offer a trade in between general purpose language and hardwired applications. Some systems like Bitcoin script are based on a general purpose language but with many control-flow structures removed. This can simplify analysis, but also removes many apps. Domain specific languages (DSLs), which like DAML, BitM, offer some flexibility, but are built around certain apps such as auctions or agreements.
Support for upgrades, reversibility, and redactions: With security in mind any language will encounter bugs and mistakes. A CBDC may decide to employ different of mitigation and remediation strategies, which may include overwriting account balances, changing the code of a smart contracts, or other modifications.
Contention and concurrency in transactions: Smart contract languages have differed in how they handle concurrent transactions and shared resources under contention. An example of a concurrent transactions reminiscent of check floating in traditional banking. Such transactions are supported in cryptocurrencies like Ethereum accounts, as with checks in the regular banking. It works because the identifier for the account does not depend on its history of transfers.
In contrast, with digital assets based on Unspent Transaction Outputs (UTXOs), such as Bitcoin, a transaction must refer to the prior transfers that provide the source of funds. In a UTXO-based digital asset, The account user cannot initiate transaction until after a withdrawal is authorized. The UTXO model is a restrictive case of account model, which can avoid some potential hazards or delays but that also limits the ability to implement mechanisms like auctions through the smart contract system.
Smart contracts acceleration of systemic risks: smart contracts may function exactly as intended by their authors, but when interacting together they lead to systemic hazards. Some set of smart contracts, such as stablecoins and other decentralized finance (DeFi) instruments, are highly interdependent, and rely on each other as collateral. It is difficult to identify when the conditions are ready for cascading “bank runs” on these instruments. An example of systemic risks brought by smart contracts is the use of “flash loans” in price manipulation attacks. Flash loans are a smart-contact enabled loans, with no clear analog in traditional finance. In a flash loan, a user offers digital assets for a limited range of “zero counterparty risk” uses. The rules of the smart contract ensure the funds that must be borrowed and repaid within the timespan of a single transaction.
Limitations of enforcing policies through CBDC restrictions: CBDC cannot limit the unsafe use of assets by restricting the smart contract language. However, simple languages can be expanded smart developers, even in ways that are not supported. For example, basic digital assets with only a plain digital signature can be enhanced with threshold signing (Section 5) without the platform support. A CBDC may collaborate with regulators to limit such use, but enforcement may be outside the limits within the system.
Favored smart contracts that are offered provided by the CBDC, may be developed by by third party developers. This how it works, with stablecoins like Coin base’s USDC. This is backed by deposits of dollars by Coin base hence relies in trust in them to manage them. limiting the CBDC to improve safety may create users to services outside the influence of the central bank. This may be an argument in favor of the CDBC providing smart contract features. We think this is a reason why not to include with the CBDC.
7.2 Off-chain protocols and cryptography
Smart contracts are part of software collection that build the apps. Web-based user interfaces can contain bugs and create errors. The CBDC should consider safety analysis standards for these software codes.
For example, to support rapid micropayments that faster than what is provided directly by the platform, smart contracts can enable off-chain payment channels, which involves a the contract working with digitally signed messages between parties. Off-chain operations should be scrutinized to the same degree as the smart contract.
7.3 Smart contracts as a two-layer architecture
With a CBDC two-layered system, the central bank issues tokens to banks who maintain the digital wallets and author the smart contract languages. The central bank can set a minimal collection of features necessary to support the funds transfer between the layers, the rest of operation is developed by the banks.
One solution to consider is that each bank, including the central bank, maintain their own instances of a blockchain. The question then is how to manage the assets transfer from one chain to another. There has been significant research on defining protocols for interoperability across independent blockchains, such as HyperService, Aspen, Interledger, Cosmos, Protean, and sidechains [177], [201]–[203]. The basic idea is that digital assets on Blockchain A can serve as a backing store for shadow assets defined on Blockchain B.
8. Secure Hardware
The role of secure hardware in digital currencies is a controversial and misunderstood topic. The authors provided a brief introduction secure hardware technology and outlined benefits and limitations of the current variants. They also make recommendations regarding secure hardware utilization for organizations like central banks.
8.1 Brief on secure hardware
Secure hardware can enable major security improvements compared to execution on standard REE In such systems, the security relies on the trustworthiness which includes an operating system (OS) with millions of lines of code, and the system operator system. When the same application is executed inside secure hardware, its security relies only the app code itself and the reliability of the hardware technology. Figure 7 shows the various protections.
Secure hardware variants: can be realized in two ways. one is a separate module, or a chip connected to the rest of the system over an interconnect. (Figure 7 right). The second, is to enhance the CPU with TEE. The code executed inside the TEE is protected, with hardware and software enforcement, from other untrusted code that runs on the REE. (Figure 7 middle). In PCs, the main widely secure hardware is Intel’s SGX [205]. It creates a TEE enclaves, which are protected from other code running on REE. SGX enclaves are supported by all latest Intel CPUs and the SGX architecture is open and allows third parties to develop their own enclaves.
Figure 7: In standard computing shown (left), the OS must be trusted for security-critical applications. In platforms with TEE capabilities (middle), it is sufficient to trust the application’s code and the hardware. In dedicated security modules (right), the added hardware and application code must be trusted. The trusted components in all three models are shown surrounded by a dashed border.
Most smartphones support two types of secure hardware. One type are equipped with (SIM card) which are closed systems, as installing new code inside them requires permission from its issuer (mobile network operator). Second, many smartphones support ARM TrustZone which realizes a TEE on the CPU of the mobile device. Permission Te mobile device vendor approval is needed to run new apps inside a TrustZone TEE, hence they can be considered a closed systems.
Hardware secure modules (HSMs): Security-critical server platforms often use external HSMs. Compared to the above commodity secure hardware, modern HSMs are specialized and expensive hardware and typically provide protections against physical tampering and other attacks. Other secure hardware include portable standalone devices that store cryptographic keys for use cases two-factor authentication and cryptocurrency client credential storage [].
Security properties: secure hardware designs realized as a separate chip or integrated in the main CPU, have data confidentiality to protect secrets from leaks, The second is integrity, hardware can guarantee that the intended code run correctly. A simple way to realize integrity is to use closed secure hardware systems where only pre-vetted code is executed. In such systems the code integrity is based on trusted authority like the secure hardware vendor. Another, flexible solution allows running code inside the secure hardware, and lets other parties verify the code correctness of the code remote attestation [209], which is good protocol that can run between the secure hardware and a remote verifier. The secure hardware is trusted (attested code faithfully, and thus ensure integrity.
8.2 Limitations of secure hardware
Secure hardware can enable significant security benefits, as long as the protections of the secure hardware itself hold. In this section we discuss possible adversaries attempt to break secure hardware protections and the estimated feasibility of such attacks.
Software-based side channels: One attack to secure hardware is through side channels. TEEs like Intel SGX and ARM TrustZone share their hardware with the rest of the computing platform, which creates a potential susceptibility to side-channel attacks, where malicious software on the CPU attempts to infer secrets that are processed inside the TEE based on utilization of shared physical resources. Research have shown the possibility of leakage from SGX enclaves [210], [211]. In addition, subtle side effects of transient execution can leak secrets to untrusted software on the same platform [212], [213].One possible defense against side-channel attacks is to write code that includes defensive measures such as elimination of secret-dependent branching. Tools that help developers to harden enclave code against side-channel attacks are an active research [214], [215]. Perfect elimination of all sources of leakage is hard, but code hardening can be an effective against most known software-side-channels.
Physical tampering: when the adversary has physical access to the secure hardware, physical attacks become strong concern. TEE architectures like SGX and TrustZone, store and process secrets inside the main CPU package. Physical attacks that attempt to extract secrets like cryptographic keys from the CPU package are generally difficult and expensive, but full elimination of all physical side-channel leakage is difficult [216]. Most smart card vendors count physical key extraction and side-channel attacks as part of the threat model and include protections. Research have shown that well-resourced adversaries (equipped with sophisticated laboratory equipment) can extract secrets from smart cards [217]–[219]. Such attacks are not likely feasible to many adversaries. HSMs include sophisticated and expensive physical protections in their manufacturing and are considered difficult to tamper with.
Trust concerns: Besides the above attack vectors, another concern for the use of secure hardware is the trust model, where the hardware vendor must be implicitly trusted. The TEE architectures system designers have little choice in terms or which secure hardware to use or which vendor to trust. Such trust issues are underscored because the designs details of TEEs are not entirely public.
8.3 Problems of simple use
Simple design: Consider a token-based digital currency system where a trusted bank issues signed coins to users. One user, can perform a payment by passing the sufficient number of coins (tokens) to another user. The recipient accepts the coins by checking the bank’s signature on each coin, but he does not need to contact the bank. In such design payments can take place offline, and they get strong privacy guarantees, as no third party is involved. The main issue with any token-based design is the possibility of double spending.
Main problems: simple use of secure hardware technology has serious problems. One it creates economic incentives for users to attack their own secure hardware. When the adversary is the owner of the computing platform, he typically has strong control over other software running on the platform and has physical access to the secure hardware. Such aspects may make attacks easier to exploit. Attacks against secure hardware become economically viable if the attacker gains large benefit. Another problem it does not support graceful degradation. Even if only one secure hardware environment gets compromised, the adversary can spend the same tokens unlimited number of times and break the system completely.
8.4 Ways to leverage secure hardware
Examples where the security of the entire digital currency system does not rely on the secure hardware and platform owners do not want to attack their hardware.
Infrastructure hardening: the backend infrastructure of a digital currency system as a complementary defense in-depth security mechanism. Assume system where a bank maintains an account balance for each user. Critical data repositories are typically replicated among multiple servers (consensus nodes) using a Byzantine-fault tolerant (BFT) protocol (Section 3). Each node stores its credentials and execute the consensus protocol within a secure hardware. Such protection mechanism make it harder for attacks.
Efficient privacy: Many systems use cryptography for user privacy protection (section 6). Zcash for example [168], is based on a distributed ledger where all transactions are stored in encrypted format using zero-knowledge proofs for transaction correctness without revealing details. The main problem is complexity. Secure hardware can simplify the procedure.
Compliance rules: CBDC deployments should, protect user privacy, enforce compliance policies, and audit mechanisms. supporting both simultaneously is a conceptual and technical challenge. One possible solution is to leverage sophisticated cryptographic constructs such as zero-knowledge proofs that allow users to show their payments are compatible with compliance rules without revealing their identity or other transaction details. However, such schemes need complicated deployment and have poor performance. Secure hardware allows for simplified systems where compliance policies are enforced without violating privacy.
Lightweight clients: systems that store transactions on a public ledger have benefits like public verifiability, but that entails heavy downloads. Selective downloading of relevant transactions might reveal identity even in systems with strong cryptographic protections. In such situations, clients can send encrypted queries to secure hardware server that has access to the entire ledger. The hardware can return the relevant transactions back,
Hardware wallets: Similar to infrastructure hardening, secure hardware can be used to harden the client devices. Systems where client credentials are protected by secure hardware (hardware wallets) are already used in permissionless cryptocurrencies, like wallets produced by Ledger [226] or Trezor [227]. They do not solve all problems of key management and payment safety: users should be careful when confirming transactions details and should have a backup if they lose the wallet.
Smart contracts: CBDCs might support complex applications deployed as smart contracts (Section 7). A problem with the current solutions is that all contract data is recorded on a public ledger. This prevents deployment of applications that require confidential contract data. Secure hardware can help enable an easier way to execute smart contracts with confidential data [180].
8.5 Summary and recommendations
Secure hardware is not a heaven for digital currency The currently available secure hardware technologies offer good but limited benefits compared to standard programs. Solutions where integrity and security depends solely on secure hardware are risky. Still, they offer benefits. When deployed carefully secure hardware can replace cryptographic protections or acts as a complementary. Investigating the possibility of CBDC deployments should consider the benefits of secure hardware. [Built-in cryptographic hardware is more powerful than both 8.5].
9. Novel Financial Technology
A retail CBDC offers many benefits: (i) gains in transactional efficiency: higher speed, lower cost, and finality, (ii) broader tax base, and reduced tax evasion, (iii) backstop to private sector managed payment systems, and (iv) enhanced financial inclusion. In principle the implications of CBDC for monetary policy and financial stability. CBDC can enable mechanisms that are similar to the current ones, but novel in terms of their achievable parameters. CBDC offers a range of innovative policies that operate at finer granularity, with better transparency, and complex program logic compared to the current financial systems. These opportunities have implications for both the deployment and transmission of monetary policies. There are also a few risks.
9.1 Implementing monetary policy
The authors think the basics of monetary policy deployment will not be affected by a switch from physical currency to CBDCs. Given that a relatively modest share of the supply of broad money is in physical form, this should not be surprising. However, other technological changes that are likely to affect financial markets and institutions could have significant effects on monetary policy execution.
Retail CBDC disseminated through electronic wallets would make it easier to implement monetary policy more effectively. First, the nominal zero lower bound, which became a binding constraint for traditional monetary policy during the worst of the global financial crisis, would no longer apply. The central bank can institute negative nominal interest rate by reducing balances on these electronic wallets at a preannounced rate.
In an economy with physical cash, this should not be possible since consumers have the alternative of holding physical currency banknotes, a zero nominal interest rate instrument. In no zero-interest central bank-issued alternative such as cash, it is easier to implement a negative interest rate. If a CDBC co-existed with cash, there would be a limit (determined by cash storage costs, frictions in the use of cash etc.) to how low the central bank could drive the interest rate. In principle, negative nominal interest rates that may become feasible with certain forms of CBDC should encourage consumption by making it expensive for households to maintain cash positions. [This is unusual thinking]. Monetary policy can be implemented through “helicopter drops” of money, once considered a remote possibility of increasing cash holdings in a non-distortionary fashion by making lump sum transfers to eligible individuals or households [irresponsible]. This is easy to implement, at least in principle [if the state has the means to force on people 9.1] if all citizens in an economy had official electronic wallets and the government transfers central bank money into those wallets. Injecting outside money into an economy quickly and efficiently become important for weak economic activity or looming crises, when banks might slow down or even terminate the creation of outside money. [So no cash puts the economy under the mercy of a group of lunatics 9.1].
One challenge: if a CBDC is issued through a two-layer approach where digital wallets are maintained by commercial banks, individuals or households might maintain multiple wallets at different institutions. Some coordination is needed to avoid double or multiple dipping from helicopter drops of money. This can be avoided if the central bank directly manages identities and accounts. In both cases, however, there would be adverse implications for privacy. Thus, a central bank could substantially reduce deflationary risks by resorting to such measures in order to escape the liquidity trap that results when it runs out of room to use traditional monetary policy tools in a physical cash-based. economy.
There is an important asymmetry in this context that could become even more consequential if outside money have only a small role in the money supply. In such case, if banks expand outside money rapidly at a time of strong economic activity with rising inflationary risks, the central bank’s ability to shrink electronic wallets holding CBDC might not do much to control the overall money supply. Although most central banks now use price-based monetary policy measures (policy interest rates) rather than quantity-based monetary policy measures, this might be another reason for central banks to issue CBDCs rather than letting central bank money wither away if households were to use less and less cash. [Blatant control 9.1]
A flip-side: where a central bank can increase or decrease the supply of outside money. The ability to impose a haircut on CBDC holdings or increase them rapidly in case the government applies pressure on a central bank to monetize its budget deficit, could lead to substitution away from the CBDC.
The reduction in nominal balances and the erosion in their real purchasing power through monetary injections can have similar effects—decreasing confidence in the currency as a safe asset that can hold its value, at least in nominal terms. This could pose potential risks to monetary stability.
Transparency: With broad adoption, retail CBDC may capture a significant segment of economic activity at a national levels or global reserves. Data harvested from the resulting panoramic view of monetary flows on the underlying ledger can provide policymakers with unprecedented data and insights. One consequence, as noted above, is an ability to limit tax. A government implementing a CBDC is better positioned to implement policies like this at large scale.
The ability to monitor monetary expenditures at individual consumers levels is already available to credit-card issuers and provides predictive power. A CBDC that overlaps with private payment systems can potentially relay the result of detailed analytics in real or near-real time to monetary policymakers.
Naturally, there is a tension between transparency and privacy Given the potential scale and scope of CBDCs, however, an analytics system with global view of transaction data—or metadata—could be repurposed as or support mass surveillance tools. Consequently, it is of vital importance that the transparency benefits of CBDCs be balanced against and leveraged with an eye on privacy requirements.
9.2 Non-fungible money
Certain forms of CBDC permit the implementation of monetary policy that affects accounts or units of money selectively and conditionally, that is, in a non-fungible manner. Money transmitted in “helicopter drops,” for instance, can carry spending conditions that permit only certain classes of expenditure. To amplify their effect in stimulating economic activity, lump sum transfers might for example carry the requirement that they be spent on, e.g., durable goods, as such spending has been shown to demonstrate limited responsiveness to economic stimulus during recessions [238].
A related issue is whether nonbank and informal financial institutions, such as Fintech lending platforms, are less sensitive to policy interest rate changes than traditional commercial banks. If these institutions do not rely on wholesale funding and have other ways of intermediating between savers and borrowers, then the central bank might face significant challenges to the effectiveness of monetary policy transmission. The relative low sensitivity of the nonbank financial sector to changes in policy needs demands further study as the structures of financial systems undergo changes that could significantly affect the implementation and transmission of monetary policy.
9.3 Some academic literature:
has only recently started to deal with the implications of CBDC and financial technology. Some authors think a CBDC will not strongly affect the implementation of monetary policy, albeit there could be some macroeconomic effects. The conclusions depend greatly on the model structure and the how the CBDC is introduced into the economy. [Sure, that would make a big difference 9.3].
9.4 Smart contracts novel capabilities
Beyond non-fungible units of currency, CBDC platforms that incorporate or serve as a substrate for smart contracts can realize a range of monetary policy tools and financial instruments. Such instruments could serve as new conduits for monetary policy but could also fundamentally impact monetary policy transmission. Experience with smart contract platforms as Ethereum shed light on the possibilities for new financial instruments. It also highlights the questions if these instruments can surface around platform control and governance.
Atomic and instantaneous execution: Most smart contracts permit multi-step transactions to execute atomically, that is all or none manner. In a serialized DLT in which transactions are fully ordered, and processed serially, no changes to the state from other transactions can occur at the same time.
Decentralized Finance (DeFi): In the model of smart contract execution, they run autonomously. They take the form of unmodifiable code that may be called by any user. This execution model is critical if smart contracts to realize their intended role as virtual trusted third parties. Risks of smart contracts’ autonomy is their ability to realize financial instruments or markets that run programmatically outside the control of contract creator any other single entity, resulting in in execution and enforcement problems in terms of unavailable in conventional contracts.
Distributed Autonomous Organizations (DAOs) was launched early in the history of the Ethereum blockchain. It implemented a form of crowdsourced venture fund, allowing users to invest money in the contract and vote on the allocation of the resulting money pool. They accumulated some 15% of all the cryptocurrency in the ecosystem. (vulnerability that caused the failure of The DAO, section 7) The DAOs are one design pattern for decentralized finance (DeFi),
Challenges and questions: cryptocurrency-based smart-contract system Ethereum is decentralized ton a degree a CBDC cannot be. Smart contracts still make it easier to create financial instruments with shared or ambiguous. The rules and governing regulations as a whole then become critical in assuring integrity. Questions include:
- Accountability: Should all smart contracts be required to have owners who assume responsibility and liability for their effects in the system? How will these owners be identified?
- Oversight: Should they be instrumented by design with reporting functionality for regulators? What privacy considerations come into play?
- Functionality: Should they have the richest possible functionality supported by the underlying DLT, or should their functionality be constrained.
- Intervention: Under what circumstances would a CBDC central bank intervene should code running on the underlying DLT prove buggy, fraudulent, criminal [262], or problematic.
Such questions arise even in CBDC designs where smart-contract functionality is overlaid on a DLT by third parties, one option considered [10], as application- layer functionality can have a systemic impact on the currency.
9.5 Summary
Opportunities may be summarized as follows:
- Implementing monetary policy: CBDCs offer the possibility of creating currency with nominal negative interest rates, as a means of stimulating consumption.
- Monetary policy transmission: Should banks and other major financial institutions be able to create payment and settlement mechanisms among themselves with suitably strong transaction confidentiality, they could assume many of the settlement and liquidity management operations that are traditionally the province of central banks. CBDCs could thereby potentially blunt central banks’ ability to transmit monetary policy.
- Smart contracts for other novel capabilities: By acting as a substrate for smart contracts, CBDCs could provide a way to translate a variety of financial innovations arising in cryptocurrency-based platforms into a setting more closely aligned with existing regulatory and legal systems.
Risks:
- Privacy concerns: A richly featured platform, with a global analytics capability, ability of operators to gather information about end users can resemble or extend beyond those discussed in section 6.
- Micromanagement: The rich range of policies realizable by highly targeted capabilities of non-fungible currency and smart contracts can tempt policymakers into interventions that are complex and representative of special interests or influence consumer behaviors that infringe on civil liberties or are otherwise harmful.
10. Legal Considerations
10.1 Jurisdiction
A CBDC is a national institution by definition and will connect with its nation’s laws and legal system. On the question of which laws and legal system take priority in case of international disagreement for each nation it own. Parties to foreign disputes want the CBDC’s own institutions to enforce those orders, but they must first accept they judgment in a court within the CBDC’s own national legal system. That said, in a federal system such as the United States or the European Union, the CBDC will still be exposed to many subnational jurisdictions with varying laws.
[That is the assumption. But there are certain enough interconnections and global orders that would like to see a universal CBDC governing the world monetary system like the world bank or the UN security council. Due to power influences of strong currency like dollar on the world other economies some planners think a universal CBDC can replace the $ and all other currencies following the example of the euro. In that sense it is not reasonable to ignore the evolution path when evaluating the realization of the CBDC experiment 10.1].
Assuming the need to deal multitude of national system Some thought should made on how to authenticate orders and verify the authority of the courts issuing them. Two options to simplify this task are to centralize all orders affecting CBDC assets in a single national tribunal ( how to stop centralizing national then world bank), or to require such orders to proceed through a common procedures before CBDC administrators act on them.
10.2 Compliance
Money laundering is is one of the recurring violation from all over the world it has been around since eternity. And with bank notes it was easier than with gold and it is expected tp become even more easy with digital currencies.
Governments prohibit laundering because it makes it easier for criminals penetrate and eventually control the economy In addition governments prohibit support terrorist groups. Anti-money-laundering and countering the funding of terrorism (AML/CFT) laws come in three levels:
1. General prohibitions, like the Money Laundering Control Act, by prohibiting the use of financial transactions to conceal the source of proceeds of criminal activity. Examples include spending cash received from drug dealing at a front business or making wire transfers legitimize kickbacks.
2. Reporting requirements, such as the Bank Secrecy Act (BSA), which requires financial institutions to report to the government all transactions in cash over 10,000 USD or more.
3. Anti-evasion rules that prohibit circumventing reporting requirements, by dividing large transaction into smaller ones less than reporting threshold.
A two-tier CBDC in which the core digital currency is traceable can meet the requirements of existing AML laws. The institutions which provide customer accounts would implement all reporting requirements under BSA, KYC, Regulators can monitor transactions entering the system and trace funds as needed. Centralization of a single transactional ledger enhances monitoring, making the CBDC unattractive for money laundering. [And for other legal matters too 10.2].
Other CBDC designs raise serious AML issues. Designs that allow for the mixing of transactional inputs or with weak identity verification AML enforcement more difficult. Designs with strong untraceability are almost certainly incompatible with AML. This may be considered a virtue from their designers’ privacy-oriented perspective, but is a deficit for the financial regulator of a CBDC.
10.3 Privacy
A US CBDC must comply with privacy mandates including protections under the General Data Protection Regulation (GDPR) and Gramm-Leach-Bliley Act (GLB) and other state laws in the US. The following mandates must be observed.
Purpose Limitation: Under GDPR personal information may only be used for the purposes the are collected for New uses require new consent.
Disclosure Limitation: Under GLB consumers have a right deny the disclosure of personal information disclosed to unaffiliated third parties. Under GDPR, such disclosures cannot take place without affirmative opt-in consent.
Access and Portability: Under GDPR subjects have right to obtain any information in a structured digital format so that they may give that data to other services.
Rectification: under GDPR subjects have the right correct any erroneous data concerning him or her.
Security Breach Notices: The GDPR and American state laws give subjects the right to be notified promptly if their data security is breached.
Some of these privacies strongly constrain the design options for a CBDC. It is not clear, if a CBDC built around a public blockchain can ever comply with the GDPR’s rules on disclosure limitation and rectification. Others require particular features in a CBDC rollout: any system that handles accounts for individuals, for example, will need to be designed such that it is possible to generate and send breach notifications if needed. Conclusion CBDC work against privacy laws.
10.4 Fraud and mistakes
CBDC legal regime must balance two concerns: preventing and correcting incorrect transactions. These transactions fall into recurring patterns, including:
1. Disloyal Agents: People frequently authorize others to act on their behalf. Whenever an agent is authorized to take some action affecting a CBDC, the agent may exceed its authority and engage in unauthorized transactions.
2. Impersonation of an authorized user by an unauthorized one.
3. Mistakes: Phishing and related attacks induce users to engage in intended transactions with unintended parties, and sometimes parties make incorrect transactions even when there is no malicious intent
CBDC needs an appropriate management infrastructure that can identify and reporting out its state to appropriate authorities.
10.5 Liens
Most property kinds can be used as collateral for debts. Legally, the creditor can hold a lien in the property where it can be seized to satisfy the debt. Some liens are possessory, e.g., a margin loan is collateralized by securities deposited with a broker. Others like mortgages, are not where the debtor retains possession and control of the property. Some liens are created by the parties as part of a loan, and others arise by law. For example, unpaid taxes on property may give the government a tax lien against the property, or a person who wins a lawsuit for damages can obtain a judgment lien over the defendant’s assets. Creditors can typically seize the defendant’s property, subject to conditions. Liens give secured creditors priority over other creditors, come with expedited procedures for a creditor to proceed quickly against the property subject to the security interest
The widespread use of liens impacts CBDC design: First, it raises doctrinal questions of how CBDC accounts and related assets should be treated as collateral. How can liens in them be created, and how can they be repossessed and foreclosed. Existing law on security interests vary greatly by type of property, even within a jurisdiction, which means that categorization questions matter greatly. If the default legal regime that would govern CBDC assets is unclear or undesirable, then legislation to establish more appropriate treatment will be necessary. Second, the CBDC’s design should facilitate the use of security interests to integrates smoothly with the rest of the financial and legal system, while excluding CBDC assets from the lien system is doctrinally possible this would be a complete non-starter for many institutions. For one thing, CBDC assets which can never be pledged as collateral for loans are worth less to borrowers; Assuming, that CBDC assets will need to be part of a secured credit system, the following are a few of the regulatory and design considerations involved.
- Collection A mechanism for the satisfaction of debts from CBDC assets. The most basic considerations here are similar to those above.
- Locking to prevent the assets from transfer without the consent of the creditor. Designers should consider whether this is a use case the CBDC should support. If so, then it requires an appropriate interface to receive and authenticate locking orders. this gives an advantage of hybrid two-tier system, A one-tier centralized ledger needs building a similar infrastructure, while a decentralized ledger would require an interface to register creditors’ claims that enable locking assets under certain conditions. Forward-looking remedies provide further challenges. Garnishment, for example, can attach to wages as soon as the debtor becomes entitled to them. This requires locking be attached to a user’s CBDC account, not just to specific CBDC assets.
- Notice Liens are invisible and intangible. But people considering buying or lending against property want to make sure that there are no liens they don’t know about. This raises the question of how to provide effective notice to third parties. Under United States law, the validity of security interests against third parties often depends on “perfection,” which roughly requires giving specific statutorily required forms of notice. A CBDC’s designers should give thought to how liens in CBDC assets should be communicated to third parties.
10.6 Tracing
Some kinds of property like cash, are considered fungible. Ancient art are treated as unique. The difference is the is how the legal system can trace their ownership through multiple hands. Tracing asserts that one particular aspect of an asset’s identity –its transaction history. Tracing may be necessary when the property has been stolen and the original owner claims it from a downstream transferee, or when it was subject to a lien and the creditor seeks to obtain it from the transferee. Different CBDC designs can facilitate different traceability, with important implications for legal treatment. Traceability provides simplicity and clarity when unwinding tainted transactions. It reduces the need for the legal system to apply crude approximations. On other hand, the no tracing can provide clarity for transferees. They do not need to check the long history of assets they are receiving for fear of taint along the chain of title. This is a chief advantage of cash: except in the crude cases, cash provides a reliable payment mechanism from the recipient’s perspective. CBDC design should consider the advantages and disadvantages of traceability in light of their legal consequences.
10.7 Taxation
The general rules of taxation apply smoothly to CBDCs. For example, in computing a person’s income from the sale of property, they typically can deduct the purchase price (or “basis”) of an asset from the sale price in computing their gain or loss. Nothing in a CBDC design is likely to disrupt such bedrock principles.
10.8 Conclusion
Current legal requirements are easiest to meet using two-tier CBDC design, where banks manage digital wallets for individuals and entities. These banks have the infrastructure to support oversight and reporting, freeze and transfer assets when required by law, and perform extensive customer service. A design where users directly interact with a CBDC managed by a central bank requires extensive interface with the legal system. A decentralized system where institutions or central bank administrators cannot directly modify the state of CBDC assets would require extensive and controversial legal changes.
11 Libra and Digital Yuan
Libra and the digital yuan have played significant role in in promoting the global CBDC vision. By examining their designs the authors see the need for a highly scalable digital currency.
11.1 Libra
With the scale and resources of a strong group of participants, the Libra Association has set lofty goals for its role. Libra’s goal is to give access for 1.7 billion unbanked. It hopes to simplify transactions to be message like. Even without central bank backing, the Association has resources to disseminate its technology across national borders and influence the global digital money spending. [That strength and extensiveness without reference of an elected authority raises concern where this global power that can define the outcome of national central banks 11.1].
Financial model: Facebook backed a cryptocurrency Libra controlled by the Libra Association based in Switzerland with a governing board of 27 corporations in tech, finance, and nonprofit. [So it is an ideal Global multinational monopoly acting across national lines 11.1]. The Libra initial white paper was published June 2019 and a second one in May 2020 detailing plans for the cryptocurrencies [20].
Libra wants to produce single-currency stablecoins, that exactly match the value of world fiat currencies. (e.g., LibraUSD or ≋USD, LibraEUR or ≋EUR, LibraGBP or ≋GBP, LibraSGD or ≋SGD). Each stablecoin will be backed 1:1 by cash reserves, cash-equivalents, and short term government securities denominated in that currency.
[It looks more of Exchange service basically than a true cyber currency. The cypher part is to allow entrance across national lines without major legal responsibilities. While having the cryptocurrency minimum protection assurances from error correction 11.1].
Basing their future work on an ultimate issuance of CBDC by world central banks, Libra hopes to integrate them directly into the their network [and become the world central bank albeit voluntarily and with no legal liabilities 11.1]. It will also maintain a capital buffer, and a reserve of circulating stablecoins, to ensure solvency. It will also create cryptocurrency called the ≋LBR, which is a digital composite of the single-currency stablecoins offered, set at a fixed ratio. The ≋LBR will be administered by a smart contract. It is intended for use in efficient cross-border settlement and as a low-volatility option nations strong or stable currencies. Because it is made up of Libra stablecoins fully backed by reserves, ≋LBR will also be backed by reserves.
[The Digital Yuan nature is different from the Libra, because it is a national project representing well defined geographical jurisdiction and well defined objectives that can be backed by a well-defined legal system. Their ability to penetrate and control the rest of the world will not similar to the Libra experiment 11.1].
≋LBR and Libra stablecoins conversion to fiat currency will be handled by third party financial institutions called VASPs (Virtual Asset Service Providers), who will interact with end users. [The proposal here seems to barrow heavily from Libra model]. Wallets belonging nonfinancial institutions or VASPs are called “unhosted wallets.” who will be supported, with tight controls (transaction limits, maximum balance enforced by the protocol).
Single currency stablecoins predate Libra. Tether (USDT), a stablecoin pegged to the US dollar, currently trades on over 100 cryptocurrency exchanges. Tether’s reserves are different from Libra’s in that they allow inclusion of short term loans from third-parties in addition to cash and cash equivalents. Tether has also expanded beyond US dollar stablecoins, to assets including gold, the Chinese Yuan, and the Euro [271].
Technical foundations: The Libra system will use exclusively a fully permissioned, Byzantine Fault Tolerant (BFT) ledger/blockchain that relies on open-source software. The stated design goal for the system is to “serve as a foundation for financial services, including a new global payment system that meets the daily financial needs of billions of people.” To achieve this goal, Libra prioritizes flexibility, security, and scalability to billions of accounts in its design. Libra will support programs written in its bespoke Move programming language.The Move programming language implements custom transaction logic and smart contracts on the Libra blockchain. Its goals are safety and security, its design explicitly informed by past security incidents involving smart contracts,. Move supports operations on currency and tokens and regulatory compliance features.
Initially, Libra Association alone will publish smart contracts that interact directly with payment systems. It plans to include third parties in the future. LibraBFT using consensus protocol, is a variant of Hotstuff [28], and designed to enhance high transaction throughput and low latency. As a permissioned system, it will require relatively little energy. Its security relies on the standard BFT assumption that less than 1/3 of validator nodes, (the machines that maintain the ledger) are compromised. Validators will be approved / permissioned by the Libra Association.
Transactions are finalized when approved by a quorum of validators, and confirmed transactions are final and visible on the ledger. Due to its use of a publicly verifiable ledger, Libra will be fully auditable by law enforcement, regulators, and users, Rather than grouping transactions into blocks like previous blockchains (Bitcoin, Ethereum, etc.), the Libra blockchain will be structured as a single continuous data structure.
11.2 The digital yuan
The government backed the People’s Bank of China (PBoC) is the first major world economy to issue a digital currency. It envisions the digital currency as cash equivalent with the potential to be the first CBDC to gain global traction. Such experiment may work in a country and culture like China but may face serious problems for small nations or different cultures. [The Digital Yuan nature is different from Libra, because it is a national project representing well defined geographical jurisdiction and objectives that can be backed by a well-defined legal system. Their ability to penetrate and control the rest of the world will not similar to the Libra experiment 11.2].
They have publicly released little about it, The information available is based on news reports, official statements, and Chinese patents filed for technologies that we conjecture are related to CBDC planning.
The PBoC names their Currency as Electronic Payments (DC/EP). As implied by the name, this digital currency will be used for some payments in lieu of traditional fiat. They formed a team to explore how to issue a “legal digital tender” in 2014 [272]. One of the goals of this digital currency is to internationalize China’s the yuan, The Chinese Agricultural bank began testing a wallet application for the digital currency internally in April 2020 [2]. The mobile payment platform Alipay has also filed patents to be a likely secondary issuer of DC/EP [274].
System overview: “The DC/EP is centrally issued and widely available. They envisions it as a a substitute for cash and a status as a legal tender. The former head of the PBoC’s Digital Currency Research Institute described that the DC/EP: “one coin, two repositories, three centers.”. One coin is the DC/EP; the two repositories are the central bank and the commercial banks who will distribute the currency and individual wallets; three center refers to data centers which will perform authentication, registration, and analysis [272]”.
According to the Deputy Governor of the PBoC, “the system should operate in two tiers with two distinct layers of functionality: interaction with commercial banks and token-based interactions [275]. The PBoC is expected to issue and redeem DC/EP via large, commercial banks. The DC/EP would be token based, with banks and financial institutions circulating them. This is similar to how fiat is handled by central banks, with a two-tiered system where central banks issue and distribute currency to financial parties that the central bank can access. This tiered anonymity was referred to as “controllable anonymity,” Users enjoy some degree of anonymity with respect to other users; banks, however, have a mechanism to deanonymize suspicious transactions, in order to combat money laundering and the financing of terror- ism [282]”. [And apply any level of control they see fit. 11.2]
Account control: “A patent application filed by Alipay, using the term “controllable anonymity,” describes a mechanism for anonymity in user-to-user transactions, but does not provide any support for anonymity for the user from financial institutions [283]. A recent patent filed by Alipay describes a command-and-control architecture in which regulators can directly, instantaneously, and unilaterally freeze users’ funds. This control can change the account type belonging to a user, stop the flow of money in or out of it, and freeze part or all of the DC/EP in the account [286]. As envisaged this patent, accounts are categorized in four levels, based on the account based on the amount and anticipated usage, the user identifying information provided to open the account. Higher-level accounts offer more flexibility. A user can apply for either an “anonymous” account or an account associated real name. “Anonymous” accounts (email address or phone number, upon registration) are “low-level” in the sense that they provide only minimal functions [277], such as strict balance limits”. [Control all over 11.2].
Novel tools: “Two patent applications [284], [285] filed by PBoC in 2017 describe a cryptographic scheme, similar to Greg Maxwell’s confidential transactions [223 that hides the transaction amount in accounts or amount transferred from all parties but transaction participants. None describes technology to hide transaction graphs, like pseudonyms in transactions are recorded on the ledger. This means the ledger is private to the authorities.
PBoC patent propose an adjustment to the DC/EP supply using an algorithm tracking certain triggers, like loan interest rates [287]. They also lay the groundwork smartcards and digital wallets that a user can link directly to conventional accounts [288]. Another PBoC a patent application specifies means for the central bank to activate tokens through banks with designated interest rates based on market conditions; these interest rates functionally tag coins with repayment conditions when they are used in loans [280]”.
Uses of secure hardware: “A recent patent applications filed by Alipay show interest in embracing secure hardware, in particular Trusted Execution Environments (TEEs), in critical operations such as currency issuance. [289], [290] describe a TEE-based implementation of two-layer issuance architecture. The central bank may deploy a “front-end encryption machine” (FEM), potentially realized by a TEE, at second-layer operators. The TEE operates as a the central bank proxy. The FEM stores the central bank’s secret keys and is invoked by operators to issue and exchange digital currencies. In the second-layer issuance, 1- an operator deposits a 100% reserve at the central bank, in exchange for encrypted string receipt. 2- the operator then feeds the FEM with the receipt and receives digital tokens of equal value. The FEM also splits a large value token into multiple ones with smaller values. Commonplace use of TEEs are also mentioned in these patent applications. One application [221] describes a digital wallet design that uses TEEs to protect users’ private keys and perform offline transactions when the sender and/or receiver is not connected to the ledger. The patent implicitly assumes a perfectly secure TEE and does not address the possibility of TEE compromise or failure. For example, since private keys are only accessible to the TEE, availability failures can lead to loss of funds. TEE can support flexible access control policies [155] capable of addressing such issues”.
12. Summary Position
The authors suggest a number of topics and issues that deserve special consideration by CBDC designers.
12.1 Monetary policy considerations
The CBDC will not remove underlying shortcomings in central bank credibility or fiscal dominance that affect the cash value. Digital money is only as strong and credible as the central bank that issues it. Shifting to full digital central bank money for retail, the transition risks could be higher without stable macroeconomic and structural policies, including regulatory frameworks that are agile to recognize and handle financial risks resulting from new intermediaries. Recognizing the potential benefits, there are many issues regarding new technologies that may affect their structure and markets. Questions also rise regarding if retail CBDC will significantly affect monetary policy implementation and transmission. These uncertainties entail a cautious approach adopting. the CBDC concept.
12.2 Ledger infrastructure
Central banks may want to keep tight control over currency issuance and transaction processing, with the ability to change or reverse transactions. Such control is highly needed given the historic risks of catastrophic error in ledger based systems, and legal requirements for handling error and fraud. In principle, tight ledger control is possible for all envisioned designs, as central bank privileges can be hard-wired in. In real life permissioned ledger systems, are limited to pre-designated entities, or centralized systems are the choices. As multi entity permissioned systems have not realized extensively, the authors expect central banks will opt for centralized CBDCs. The digital yuan appears to be embracing such centrality.
Central banks may consider use of authenticated data structures (ADSs) as an extension for centralized CBDC deployments. The central bank can distribute the ADS digest 𝑅 publicly without revealing ledger contents. It can prove the inclusion of particular transactions in the ledger with reference to 𝑅 alone, and also use 𝑅 to demonstrate it is different from forking, showing different ledger contents / balances to different entities. Forking may rise as a result of operator malfeasance or a breach, hence the proving forking is prevented can strengthen users’ confidence.
12.3 Wallets funds and key custody
Cryptocurrency was built on the use of wallets and key management. To authenticate users’ transactions, it requires digital signatures which are strong tools for all computing infrastructure, and they require the secret keys. Protecting and backing up keys is a problem for many cryptography users, who tend to rely on service providers by holding users’ assets intermediaries. While CBDCs may rely on similar settings it is not clear how they can advance the goal for CBDCs of financial inclusion if consumers have to deal with middle institutions Efficient methods to custody of funds and secret keys will make a definer of the CBDC future. Some designs, such as the digital yuan, may offer limited support for user administered accounts. CBDCs would, however, make it easy to prepopulate individual accounts with funds, which would be an important first step in enrolling consumers in the financial system.
12.4 Privacy
If a CBDC maintains personal balances on the ledger, which is a prerequisite for a retail CBDC, then privacy will become major challenge. (similar to the case digital banknotes.). While there are cryptographic systems for maintaining transaction privacy in such settings, they are complex and costly, and unlikely to scale to meet the requirements of a CBDC in the short-to-medium term. One critical observation is that pseudonymous accounts, i.e., accounts with holders’ names kept secret, offer only weak privacy. Under many circumstances, as the history of cryptocurrencies shows, it would be possible to deanonymize accounts. A CBDC will reveal significantly more information about individuals’ transactions to central banks than existing systems do. This observation strongly motivates technical and legal confidentiality protections for ledger contents.
12.5 Innovation
The authors believe there is a wide range of opportunities for innovation in a CBDC beyond mitigation of frictions in transaction processing. Some derive from the assumed transparency a CBDC would afford regulators, including providing overall but fine-grained view of economic spending. They would also include new monetary policy levers, like central banks’ ability to institute negative nominal interest rates, create currency with time-limits or other spending conditions, in order to create highly needed monetary interventions in a national economy. Novel financial technologies may be best captured with CBDC support for smart contracts, which would offer a flexible means of defining policies. Others for the creation of new types of financial instruments; in cryptocurrency systems, they have led to the creation of instruments so novel (flash loans) with direct analogs in the current financial system. Given the historically demonstrated hazards of smart contract bugs (The DAO), software assurance and oversight will be of paramount importance.
12.6 Secure hardware
The authors recommend strongly thorough investigation of the utilization of secure hardware to enhance the security levels of the CBDC system. Even with vulnerabilities detected in recent secure hardware, that suggests not be using them in critical subsystems, there are many other applications it can serve well as a fast helper to strengthen or harden the systems. The paper suggested an extensive set of solutions on utilization enhancing privacy through defense-in-depth protective layer, strengthening compliance enforcement by constraining the hardware system to operate only according to regulatory rules, and to protecting the users.
12.7 Two-layer architectures
Most investigated designs focus on two-layer CBDC architectures. In such settings, existing non-governmental Payment Interface Providers (PIPs) [10] add a second layer that would represent interface between users and the central bank. Two-layer designs accommodate align existing customer service delivery and compliance mechanisms against money-laundering and illegal funding laws, this can transform the system smoothly without disturbing the existing operating banking system. These systems may not solve the privacy concerns related to representing individuals’ accounts or banknotes in the CBDC. Like if to deploy smart contracts by PIPs, instead of managing them by the CBDC, each solution might bring hidden risks for control of regulators, synchronizing different PIPs’ may prove incompatible, which needs a lot of adaptation interfaces to CBDC. Smart contract tight control by the central bank can cripple innovation. setting core technical and operating standards could prove a useful middle solution. The benefits and risks of CBDC are complex, correlations between financial, legal, and technical considerations. Nations do not have to work on a preset rules but should consider their own conditions and environments into when the design their own settings before introducing a CBDC to compare benefits vs. liabilities.
References
(1) Design choices for Central Bank Digital Currency, Policy and technical considerations. Sarah Allen, Srdjan Capkun, Ittay Eyal, Giulia Fanti, Bryan Ford, James Grimmelmann, Ari Juels, Kari Kostiainen, Sarah Meiklejohn, Andrew Miller, Eswar Prasad, Karl Wüst, and Fan Zhang.
https://www.brookings.edu/wp-content/uploads/2020/07/Design-Choices-for-CBDC_Final-for-web.pdf
(2) Central Bank Digital Currencies and the Long-Term Advancement of Financial Stability. JEREMY NEY, NICOLAS XUAN-YI ZHANG: https://assets.pubpub.org/la7h52pu/41581339058679.pdf
(3) Raphael Auer, Jon Frost, Leonardo Gambacorta, Cyril Monnet, Tara Rice and Hyun Song Shin, “Central bank digital currencies: motives, economic implications and the research frontier” , BIS Working Papers No 976, Monetary and Economic Department, November 2021. https://www.bis.org/publ/work976.pdf
(4) Kristalina Georgieva, IMF Managing Director, “The Future of Money: Gearing up for Central Bank Digital Currency Atlantic Council”, presentation in Washington, DC, February 9, 2022.
(5) Todd Keister, Rutgers University and Daniel Sanches, Federal Reserve Bank of Philadelphia, Should Central Banks Issue Digital Currency”, The Review of Economic Studies , Posted on March 23, 2022, https://www.restud.com/paper/should-central-banks-issue-digital-currency/
(6) Further references https://www.google.com/search?client=firefox-b-d&q=a+research+article+agains+tthe+central+banks+digital+currency
External references tagged in the text. Number refers to the same references of the original article
- Section 1: [1-8].
- Section 2: [8, 10, 11].
- Section 3: [17-21], [31-34] [76-78].
- Section 4: [10, 83, 91, 96, 112].
- Section 5: [144-146, 149, 152-157].
- Section 6: [10 159-151, 164, 168, 169, 173-175, 178, 182, 185, 186].
- Section 7: [177 201-203]
- Section 8: [205, 210-215, 216, 217-219, 180, 226, 227].
- Section 9: [262]
- Section 11: [20 272 274 275, 277, 282-283, 284-285, 223, 280, 287-288, 221 , 155]